Uninstaller sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. The uninstaller, a seemingly mundane utility, plays a pivotal role in maintaining the health and stability of our digital lives.
Table of Contents
From the humble beginnings of early operating systems to the sophisticated software landscapes of today, uninstallers have evolved alongside technology, adapting to meet the ever-changing needs of users. This exploration delves into the intricate world of uninstallers, unraveling their inner workings, uncovering their secrets, and shedding light on their critical importance in a world where software installations and removals are commonplace.
Uninstaller Basics
An uninstaller is a software program designed to remove other programs from a computer system. It’s a crucial tool for managing applications and ensuring a clean system.
Uninstallers are designed to remove all traces of a program, including its files, folders, registry entries, and other associated data. This process is different from simply deleting a program’s folder, as it ensures that the program is completely removed from the system.
Uninstalling vs. Deleting
Deleting a program’s folder or files does not necessarily remove all traces of the program. It might leave behind leftover files, registry entries, or other remnants that can cause problems.
Uninstallers are specifically designed to perform a thorough removal, ensuring that the program is completely eradicated from the system. This helps prevent conflicts with other programs, improve system performance, and free up disk space.
Common Uninstaller Interfaces and Features
Uninstallers come in various forms, with varying levels of complexity. Common features include:
- Program list: A list of all installed programs, allowing users to select which program to uninstall.
- Removal options: Options to remove program files, registry entries, or other associated data. Some uninstallers allow users to choose specific components to remove, such as plugins or language packs.
- Progress bar: A visual indicator of the uninstallation process.
- Log files: A record of the uninstallation process, which can be helpful for troubleshooting.
- Advanced options: Some uninstallers offer advanced options, such as the ability to remove program files from specific locations or to create a backup of the program’s data before removal.
Examples of Uninstaller Interfaces
Here are some examples of common uninstaller interfaces:
- Windows Add/Remove Programs: This built-in uninstaller provides a basic list of installed programs and allows users to remove them.
- Revo Uninstaller: A popular third-party uninstaller that offers advanced features, such as deep scanning for leftover files and registry entries, and the ability to create restore points before uninstallation.
- IObit Uninstaller: Another popular third-party uninstaller with features like force uninstallation, which can be useful for removing stubborn programs.
Uninstaller Types
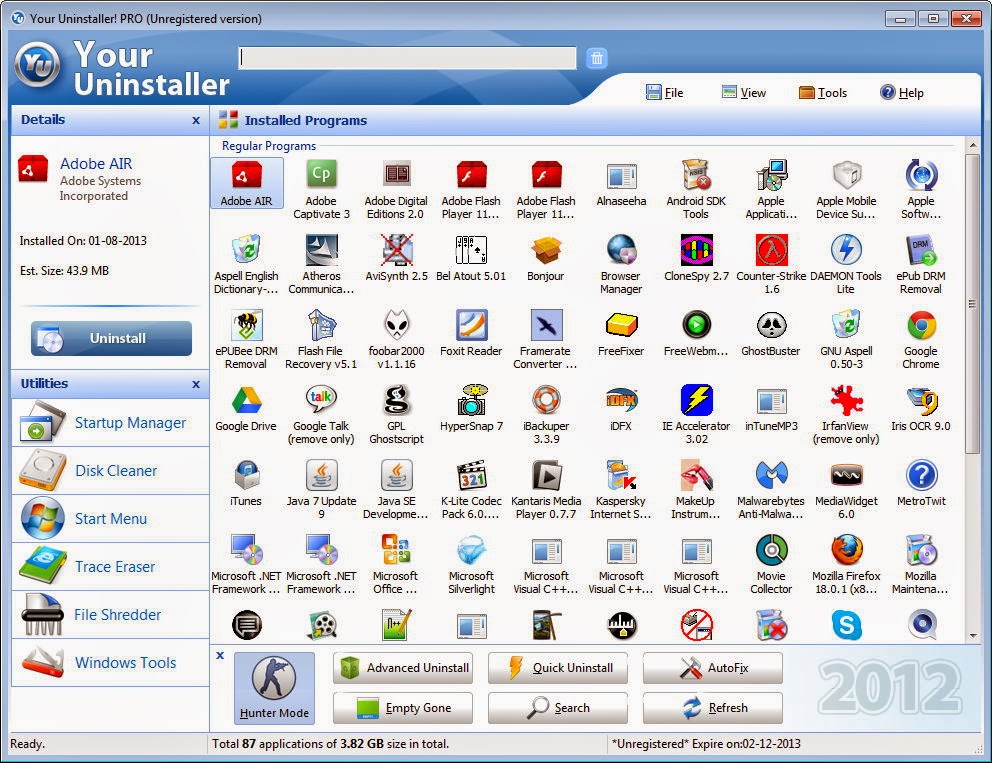
Uninstallers come in various forms, each tailored to specific needs and purposes. Understanding these types helps you choose the right uninstaller for your situation.
The most common types of uninstallers include system-level uninstallers, application-specific uninstallers, and third-party uninstallers. Each type offers unique features and benefits, catering to different user requirements.
System-Level Uninstallers
System-level uninstallers are built into the operating system, typically found within the Control Panel (Windows) or Applications folder (macOS). They provide a standardized method for removing software, ensuring compatibility and safety.
These uninstallers are designed to handle the removal of most applications installed on the system, removing associated files, folders, and registry entries. They are often the first choice for users who want a simple and reliable way to remove software.
Application-Specific Uninstallers
Application-specific uninstallers are included with the software package itself. They are designed to remove the application and all its components, including configuration files, data, and registry entries.
These uninstallers are often more effective at removing all traces of the application, ensuring a clean uninstallation. They may also offer additional features, such as the ability to uninstall multiple applications simultaneously or to export a list of uninstalled applications.
Uninstaller programs are often associated with removing specific applications, but they can also be used to clean up remnants of software, including components of middleware. This is particularly useful when a program is uninstalled improperly or when leftover files can interfere with other applications.
While uninstaller programs can be helpful for managing software, it’s important to note that they are not a replacement for proper software installation and removal practices.
Third-Party Uninstallers
Third-party uninstallers are standalone applications that can be downloaded and installed separately. They offer more advanced features than system-level or application-specific uninstallers, such as the ability to remove stubborn applications, clean up leftover files, and monitor system changes.
Third-party uninstallers are particularly useful for removing applications that have been corrupted or have been installed without proper permissions. They often provide more detailed information about the application being uninstalled, including its size, location, and dependencies.
Registry Entries and Uninstallation
Registry entries play a crucial role in the uninstallation process. They store information about installed applications, including their location, settings, and dependencies. When an application is uninstalled, its associated registry entries are removed.
However, sometimes registry entries are not removed correctly, leading to issues like application remnants, system errors, or slow performance. This is where specialized uninstallers come in handy, as they can effectively clean up leftover registry entries and ensure a complete uninstallation.
Uninstaller Processes
Uninstallers are designed to remove software from your computer in a controlled and organized manner. They are essential tools for maintaining system stability and freeing up disk space.
The uninstallation process involves a series of steps designed to remove all traces of the software from your system. This includes removing files, folders, and registry entries associated with the program.
File and Folder Removal
Uninstallers typically remove files and folders related to the software in a specific order to prevent conflicts or data loss. They may first remove temporary files or files that are not essential for the software’s functionality. Then, they may remove the main program files and folders.
Uninstallers use different methods to remove files and folders:
- Direct Deletion: The uninstaller simply deletes the files and folders from the hard drive. This is the most straightforward method, but it can sometimes leave behind residual files or folders.
- Moving to the Recycle Bin: The uninstaller moves the files and folders to the Recycle Bin, allowing you to recover them if needed. However, this method does not permanently remove the files and folders from your system until you empty the Recycle Bin.
- Overwriting with Zeroes: This method involves overwriting the files and folders with zeroes, making it more difficult to recover the data. This method is often used to ensure that sensitive information is permanently deleted.
Registry Entry Removal
The Windows Registry is a database that stores configuration settings for your operating system and installed programs. When you install a program, it adds entries to the registry that define its settings, file locations, and other information.
Uninstallers remove registry entries related to the software to ensure that it is completely removed from your system. They use various methods to remove registry entries:
- Direct Deletion: The uninstaller directly deletes the registry entries associated with the program. This method is straightforward but can potentially leave behind incomplete entries, leading to errors or conflicts.
- Value Modification: The uninstaller modifies the values associated with the registry entries, effectively disabling the program without deleting the entries entirely. This method is used to prevent conflicts and ensure that the program cannot be launched again.
- Registry Key Removal: The uninstaller removes the entire registry key associated with the program, along with all its subkeys and values. This is the most thorough method for removing registry entries but requires careful implementation to avoid affecting other programs.
Potential for Errors or Incomplete Uninstallations
While uninstallers are designed to remove software completely, errors or incomplete uninstallations can occur due to various factors:
- Corrupted Uninstall Files: If the uninstaller files are corrupted, the uninstallation process may fail or leave behind incomplete entries.
- System Conflicts: If the software is deeply integrated into your system, uninstalling it might create conflicts with other programs or the operating system.
- User Errors: Users may interrupt the uninstallation process or make incorrect selections during the uninstallation process, leading to incomplete removal.
Error Handling and Recovery
In case of errors or incomplete uninstallations, you can use various methods to resolve the issue:
- Run the Uninstaller Again: Try running the uninstaller again to complete the removal process.
- Use a Third-Party Uninstaller: Third-party uninstallers, such as Revo Uninstaller or IObit Uninstaller, offer advanced features for removing stubborn programs and cleaning up residual files.
- Manually Remove Files and Folders: If the uninstaller fails, you can manually remove the files and folders related to the software. However, be cautious as deleting incorrect files can damage your system.
- Use System Restore: If you are confident that the uninstallation process caused problems, you can use System Restore to revert your system to a previous point in time before the uninstallation.
Uninstaller Challenges
While uninstalling software seems like a straightforward process, there are instances where it can become a frustrating experience. Sometimes, uninstallers may fail to remove all traces of a program, leaving behind leftover files and registry entries. These remnants can lead to various issues, such as program conflicts, performance degradation, or even security vulnerabilities.
Dealing with Stubborn Programs
Removing stubborn programs can be a real headache. These programs often resist standard uninstallation methods, leaving behind fragments of their files and configurations.
- Incomplete Uninstall: Sometimes, the uninstaller might not remove all program files or registry entries, leaving behind remnants that can cause conflicts or performance issues.
- Corrupted Uninstall Files: Damaged uninstaller files can prevent the program from being removed properly. This can happen due to file corruption, disk errors, or incomplete downloads.
- Program Dependencies: Some programs rely on other programs or components to function. If these dependencies are not removed correctly, the uninstaller might fail to remove the main program.
- System-Level Permissions: Certain programs might have deep integration with the operating system, requiring administrative privileges for complete removal. Without proper permissions, the uninstaller might not be able to access and delete all necessary files.
- Malware Interference: In some cases, malicious software might interfere with the uninstallation process, preventing the program from being removed completely or even causing further damage to the system.
Troubleshooting Uninstallation Problems
Here are some troubleshooting steps you can take to address common uninstallation issues:
- Run the Uninstaller as Administrator: Right-click on the uninstaller and select “Run as administrator” to ensure it has the necessary permissions to remove all program files.
- Use a Dedicated Uninstaller: If the built-in uninstaller fails, try using a third-party uninstaller tool. These tools are designed to remove stubborn programs and leftover files.
- Manually Remove Program Files: You can manually delete program files from the installation directory. However, be careful not to delete any critical system files. Use a reliable file manager like File Explorer or a third-party alternative for this task.
- Clean Registry Entries: Use a registry cleaner to remove leftover registry entries related to the program. Be cautious when using registry cleaners as they can cause system instability if not used properly.
- Run a System Scan: Perform a full system scan with your antivirus software to ensure there is no malware interfering with the uninstallation process.
- Reinstall the Program: If all else fails, reinstalling the program might fix the uninstallation issue. This can overwrite corrupted files and re-register the program properly.
Uninstaller Security
Uninstallers, while designed to remove software from your system, can pose security risks if not handled carefully. Using untrusted or malicious uninstallers can compromise your system’s security and leave you vulnerable to various threats.
Importance of Using Trusted Uninstallers
It is crucial to prioritize using trusted and legitimate uninstallers to ensure the safe removal of software from your system. Untrusted uninstallers may contain malicious code that can harm your system or steal sensitive information.
- Verify the Uninstaller’s Source: Always download uninstallers from the official website of the software developer or a reputable software download platform. Be cautious of uninstallers offered through untrusted websites or email attachments.
- Check for Digital Signatures: Legitimate uninstallers often have digital signatures that verify their authenticity and integrity. Look for a digital signature icon or certificate before downloading or running an uninstaller.
- Read User Reviews: Before using an uninstaller, check online reviews and forums for feedback from other users. This can provide insights into the uninstaller’s reliability and potential security risks.
Protecting Your System from Malware Disguised as Uninstallers
Malware can be disguised as legitimate uninstallers to gain access to your system. These malicious programs can steal your data, compromise your privacy, or damage your computer.
- Be Wary of Free or Cracked Software: Free or cracked software often comes bundled with malicious uninstallers or other malware. It is best to avoid downloading software from unreliable sources.
- Scan Downloaded Files: Before running any downloaded uninstaller, scan it with a reputable antivirus program to detect any malicious code.
- Enable Real-Time Protection: Keep your antivirus software updated and enabled with real-time protection to detect and block malware in real time.
- Be Cautious of Pop-up Advertisements: Avoid clicking on pop-up advertisements that claim to offer free uninstallers or software updates. These ads often lead to malicious websites or downloads.
Uninstaller Security Best Practices
Here are some best practices to ensure uninstaller security:
- Use the Built-in Uninstaller: Most operating systems provide built-in uninstallers that are generally safe and reliable. If available, use the built-in uninstaller instead of third-party options.
- Run Uninstallers with Administrative Privileges: Some uninstallers require administrative privileges to remove software completely. If prompted, grant administrative access to the uninstaller.
- Check for Residual Files: After uninstalling software, scan your system for any residual files or folders that may have been left behind. These files can cause conflicts or security risks.
- Keep Your System Updated: Regularly update your operating system and antivirus software to protect against emerging threats and vulnerabilities.
Uninstaller Best Practices
Uninstaller best practices are essential for ensuring a clean and safe removal of software from your computer. They help to prevent leftover files, registry entries, and other remnants that can cause system instability or security vulnerabilities. Following these guidelines can contribute to a smoother and more efficient uninstallation process.
Choosing the Right Uninstaller
Selecting the appropriate uninstaller is crucial for a successful and safe removal process. The choice depends on the specific software and your individual needs. Here are some factors to consider:
- Software Type: Different software programs may require specialized uninstallers. For instance, complex applications may need a more comprehensive uninstaller than simple utilities.
- Operating System: Ensure compatibility between the uninstaller and your operating system.
- User Reviews: Research user reviews and ratings to gauge the effectiveness and reliability of the uninstaller.
- Features: Look for features such as advanced scanning, registry cleanup, and the ability to uninstall multiple programs at once.
- Security: Choose an uninstaller from a reputable source and ensure it has a good track record for security.
Ensuring Complete Uninstallation
A complete uninstallation involves removing all traces of the software, including files, folders, registry entries, and other remnants. This is essential to prevent conflicts with other programs and to free up disk space.
- Use the Built-in Uninstaller: Most software comes with a built-in uninstaller. This is often the best option for a quick and straightforward removal process. However, it may not always remove all components, especially for complex applications.
- Run a Deep Scan: Consider using a third-party uninstaller that performs a deep scan of your system to identify all remaining files and registry entries associated with the software.
- Check for Leftover Files: Manually search for any remaining files or folders in the program’s installation directory and delete them.
- Clean the Registry: Use a registry cleaner to remove any leftover registry entries. However, be cautious as improper registry modifications can damage your system.
Preventing Uninstallation Issues and Data Loss
Uninstallation issues can arise from various factors, such as incomplete removal, corrupted files, or registry errors. It’s crucial to take precautions to minimize these problems and protect your data.
- Backup Your Data: Before uninstalling any software, create a backup of your important files and data. This provides a safety net in case of data loss during the uninstallation process.
- Disable Antivirus: Temporarily disable your antivirus software, as it may interfere with the uninstallation process. However, be sure to re-enable it afterward.
- Run as Administrator: If you encounter permission errors, try running the uninstaller as an administrator to grant it the necessary privileges.
- Restart Your Computer: After uninstalling, restart your computer to ensure all changes are applied and to resolve any potential conflicts.
Using Uninstallers Effectively
Effective uninstaller usage involves understanding their features and limitations. This helps you avoid potential issues and maximize the efficiency of the removal process.
- Read the Instructions: Before using any uninstaller, carefully read the instructions and any documentation provided by the developer.
- Choose the Right Options: Pay attention to the options offered by the uninstaller, such as removing user data or keeping specific files.
- Monitor the Process: Observe the uninstallation process closely for any error messages or unusual behavior.
- Verify Completion: After the uninstallation is complete, verify that all traces of the software are removed by checking the program list, installation directory, and registry.
Uninstaller Evolution
The evolution of uninstallers has mirrored the development of operating systems and software distribution models, reflecting changes in how users install and remove applications. From simple batch files to sophisticated software packages, uninstallers have become increasingly complex and sophisticated, reflecting the growing complexity of software applications.
Impact of Operating System Advancements
Operating system advancements have significantly impacted uninstaller functionality. Early operating systems lacked dedicated uninstaller mechanisms, relying on manual file deletion. The introduction of Windows and its standardized uninstaller framework marked a significant shift. This framework enabled developers to bundle uninstallers with their applications, ensuring a more structured and reliable removal process.
The Windows uninstaller framework established a standard for application removal, paving the way for more sophisticated uninstaller features.
- Early Operating Systems: Manual file deletion, potential for data loss and system instability.
- Windows and Standardized Uninstaller Frameworks: Introduced a structured approach to application removal, minimizing the risk of system corruption.
- Modern Operating Systems: Advanced uninstallers with features like rollback capabilities, registry cleaning, and dependency management.
Uninstaller Impact
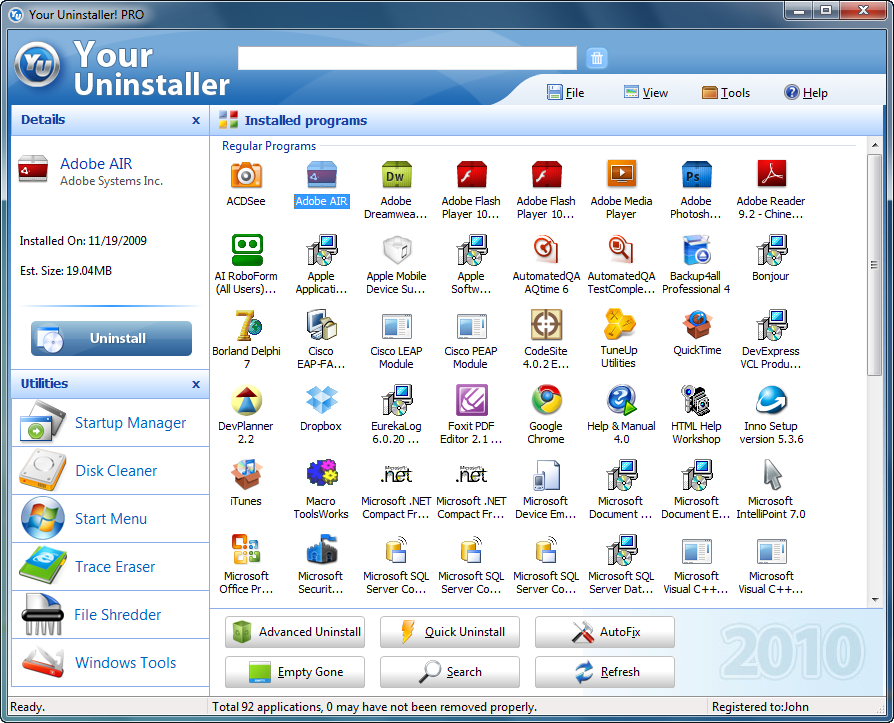
Uninstallers play a crucial role in maintaining a healthy and secure computer system. While their primary function is to remove software, their impact extends beyond simply deleting files. Uninstallers influence system performance, resource usage, and overall system health.
Impact on System Performance and Resource Usage
Uninstallers can affect system performance and resource usage in various ways. A well-designed uninstaller will efficiently remove all associated files and registry entries, minimizing the impact on system performance. However, incomplete or corrupted uninstallations can lead to residual files and registry entries, which can slow down the system and consume valuable resources.
Implications of Incomplete or Corrupted Uninstallations
Incomplete or corrupted uninstallations can have several negative implications:
- System Slowdown: Residual files and registry entries can clutter the system, slowing down startup times, program launches, and overall system responsiveness.
- Resource Consumption: Leftover files and registry entries can consume disk space and memory, hindering the performance of other programs.
- Conflicts and Errors: Incomplete uninstallations can lead to conflicts with other programs, causing errors and instability.
- Security Risks: Unremoved files and registry entries can contain sensitive information that could be exploited by malicious actors.
Contribution to Overall System Health and Security
Effective uninstallers contribute to the overall health and security of a computer system by:
- Ensuring Clean Removal: Well-designed uninstallers remove all associated files and registry entries, preventing clutter and potential conflicts.
- Reducing Security Risks: Complete removal of software eliminates the risk of residual files containing sensitive information that could be exploited by malicious actors.
- Improving System Performance: By removing unnecessary files and registry entries, uninstallers can improve system performance and responsiveness.
- Maintaining System Stability: Effective uninstallers help prevent conflicts and errors that can arise from incomplete or corrupted uninstallations.
Outcome Summary
As we conclude this journey into the realm of uninstallers, we emerge with a deeper understanding of their complexities and significance. From the fundamental processes of removing programs to the challenges of handling stubborn or corrupted software, uninstallers play a vital role in ensuring the smooth operation and security of our computer systems. By embracing best practices and utilizing trusted tools, we can navigate the world of software installation and removal with confidence, knowing that our digital environments are protected and optimized for peak performance.

