System software, the unseen foundation of our digital world, plays a pivotal role in enabling the functionality of computers and devices. From the operating system that manages resources to the device drivers that facilitate communication between hardware components, system software acts as the intermediary between user interaction and the intricate workings of the machine.
Table of Contents
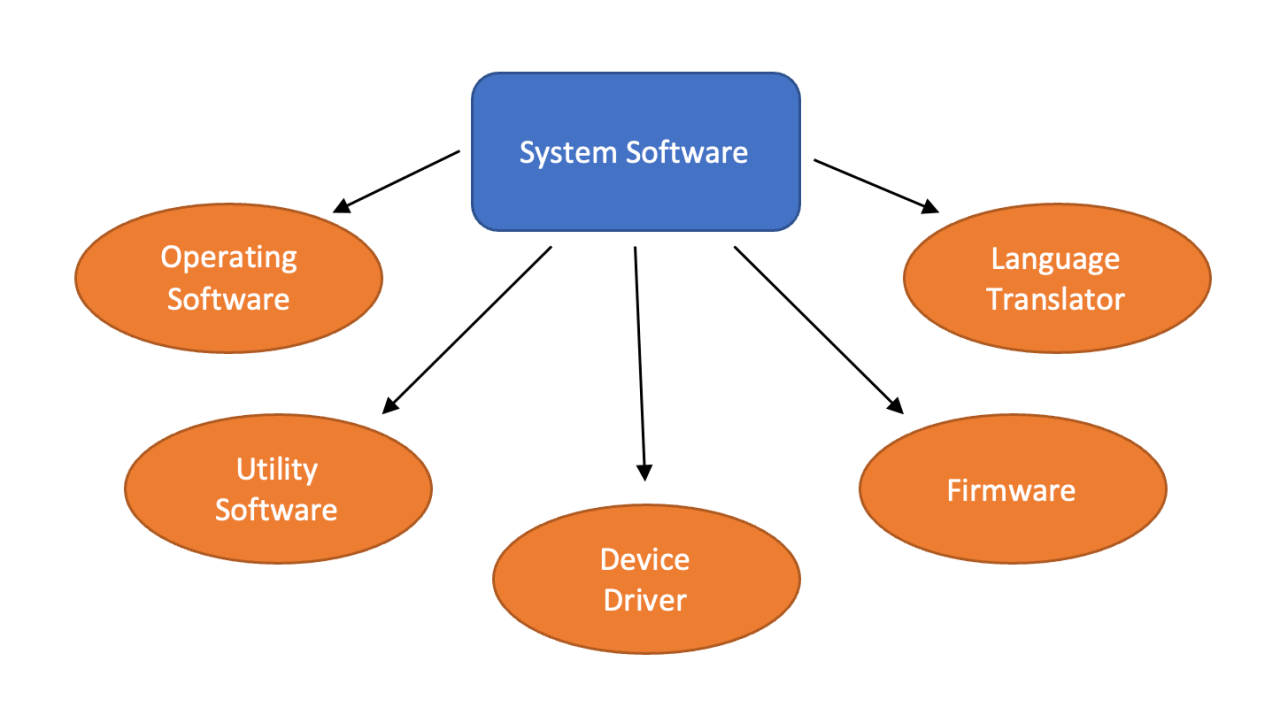
This essential software encompasses a diverse range of programs, including operating systems, device drivers, and utility programs, each contributing to the seamless operation of our computers. Understanding the intricacies of system software provides valuable insight into the fundamental principles that govern our digital experiences.
Device Drivers: System Software
Device drivers are essential software components that act as intermediaries between the operating system and hardware devices. They provide a standardized interface for the operating system to communicate with and control various hardware components, enabling the smooth operation of the entire system.
Interaction with Hardware and Operating System
Device drivers play a crucial role in bridging the gap between the hardware and the operating system. They translate high-level commands from the operating system into low-level instructions that the hardware can understand. For example, when you click on a file to open it, the operating system sends a command to the device driver responsible for the hard drive. The driver then interprets this command and instructs the hard drive to read the data from the specified location.
- Hardware Interaction: Device drivers interact directly with hardware devices, providing a way for the operating system to control and access their functionality. This interaction involves sending and receiving signals, managing data transfer, and handling device-specific operations. For example, a graphics driver interacts with the graphics card to render images and display them on the screen.
- Operating System Interaction: Device drivers also interact with the operating system, receiving commands and providing status updates. This interaction allows the operating system to monitor the hardware’s performance, manage resources, and handle errors. For instance, a network driver communicates with the operating system to report the status of the network connection and receive instructions to send or receive data.
Challenges in Development and Maintenance
Developing and maintaining device drivers can be a complex and challenging task due to the wide variety of hardware components and the constant evolution of technology.
- Hardware Compatibility: Device drivers need to be specifically designed for each hardware device, ensuring compatibility and optimal performance. This requires developers to have a deep understanding of the hardware’s architecture and functionality.
- Operating System Compatibility: Drivers need to be compatible with the specific operating system they are intended for. As operating systems evolve, drivers may need to be updated to maintain compatibility and support new features.
- Security Considerations: Device drivers can be a potential security vulnerability, as they have access to the system’s hardware and can potentially be exploited by malicious actors. Developers need to carefully design and test drivers to mitigate security risks.
- Driver Updates: As new hardware devices and operating system versions are released, device drivers need to be updated to maintain compatibility and support new features. This can be a challenging task, especially for manufacturers who need to support a wide range of devices and operating systems.
System Software and Security
System software plays a crucial role in maintaining the security of a computer system. It acts as a foundation for all other software, including applications, and provides essential services that govern how the system interacts with hardware and users. By controlling access to system resources, managing user accounts, and enforcing security policies, system software directly impacts the overall security posture of the system.
Security Threats and Vulnerabilities
System software can be vulnerable to various security threats that can exploit weaknesses in its design, implementation, or configuration. These vulnerabilities can be exploited by malicious actors to gain unauthorized access to sensitive data, disrupt system operations, or even take control of the entire system.
- Malware: Malicious software, such as viruses, worms, and Trojans, can infect system software and compromise its integrity. These threats can spread through various means, including email attachments, infected websites, or vulnerabilities in software applications.
- Exploits: Exploits target vulnerabilities in system software, allowing attackers to gain unauthorized access or control over the system. These vulnerabilities can arise from programming errors, design flaws, or outdated software versions.
- Configuration Errors: Incorrectly configured system software can create security loopholes that attackers can exploit. For example, weak passwords, open ports, or disabled security features can leave the system vulnerable.
- Social Engineering: Attackers can use social engineering techniques to trick users into revealing sensitive information or granting unauthorized access to the system. This can involve phishing emails, phone calls, or other forms of deception.
Security Measures
System software incorporates various security measures to mitigate threats and vulnerabilities. These measures can be categorized as preventive, detective, and corrective.
- Firewalls: Firewalls act as barriers between the system and external networks, blocking unauthorized access attempts. They analyze incoming and outgoing network traffic and allow only authorized connections.
- Antivirus Programs: Antivirus programs detect and remove malicious software from the system. They use signature-based detection, behavioral analysis, and other techniques to identify and neutralize threats.
- Intrusion Detection Systems (IDS): IDS monitor system activity for suspicious patterns that may indicate an attack. They can detect unauthorized access attempts, network scans, and other malicious activities.
- Intrusion Prevention Systems (IPS): IPS actively block attacks by modifying network traffic or system behavior based on predefined rules. They can prevent attacks from reaching their targets or stop malicious activity before it can cause damage.
- Access Control: System software implements access control mechanisms to restrict access to system resources based on user identity and permissions. This ensures that only authorized users can access sensitive data or perform critical operations.
- Auditing: System software can record and track system events, such as user logins, file accesses, and network connections. This information can be used to investigate security incidents, identify suspicious activity, and improve security practices.
System Software for Different Platforms
System software is designed to manage and control the hardware and software resources of a computer system. It acts as an intermediary between the user and the hardware, providing a platform for applications to run. However, the specific requirements and functionalities of system software vary significantly depending on the target computing platform. This section explores how system software is tailored for different platforms, such as desktop computers, mobile devices, and embedded systems.
System Software for Desktop Computers
Desktop computers are general-purpose computing devices that offer a wide range of functionalities and resources. System software for desktop computers is designed to provide a user-friendly interface, manage hardware resources, and support a wide range of applications.
Here are some examples of system software commonly found on desktop computers:
- Operating Systems: Operating systems (OS) such as Windows, macOS, and Linux provide the core functionality for managing hardware, running applications, and interacting with the user. They offer features like file management, process management, memory management, and device drivers.
- Device Drivers: Device drivers are software components that allow the operating system to communicate with specific hardware devices, such as printers, graphics cards, and network adapters. They translate commands from the OS into instructions that the hardware can understand.
- System Utilities: System utilities are tools that help manage and maintain the operating system and hardware. Examples include disk defragmenters, antivirus software, and system monitoring tools.
System Software for Mobile Devices
Mobile devices, such as smartphones and tablets, have become ubiquitous in modern society. System software for mobile devices must be optimized for portability, energy efficiency, and touch-based interaction.
The key challenges and considerations for developing system software for mobile devices include:
- Limited Resources: Mobile devices typically have less processing power, memory, and storage space compared to desktop computers. System software must be designed to operate efficiently within these constraints.
- Energy Efficiency: Mobile devices rely on batteries, so system software must be designed to minimize power consumption. This includes optimizing processes, managing background tasks, and implementing power-saving features.
- Touch-Based Interaction: Mobile devices primarily rely on touchscreens for user input. System software must provide a user-friendly interface that is intuitive and easy to navigate with touch gestures.
- Connectivity: Mobile devices are often connected to the internet, which presents challenges for system software in terms of security, data usage, and network management.
Here are some examples of system software commonly found on mobile devices:
- Mobile Operating Systems: Mobile operating systems, such as Android and iOS, are specifically designed for mobile devices. They provide a user-friendly interface, manage hardware resources, and support a wide range of mobile applications.
- Mobile Apps: Mobile apps are software applications designed for mobile devices. They offer a wide range of functionalities, from communication and entertainment to productivity and utility.
- Mobile Security Software: Mobile security software is designed to protect mobile devices from malware, viruses, and other threats. It typically includes features such as antivirus protection, data encryption, and anti-theft measures.
System Software for Embedded Systems
Embedded systems are specialized computer systems designed for a specific purpose. They are typically found in devices such as automobiles, appliances, medical equipment, and industrial control systems. System software for embedded systems is highly customized and optimized for the specific requirements of the target device.
The key challenges and considerations for developing system software for embedded systems include:
- Real-Time Constraints: Embedded systems often have strict real-time requirements, meaning they must respond to events within a specific time frame. System software must be designed to meet these deadlines, even under heavy workloads.
- Limited Resources: Embedded systems typically have limited processing power, memory, and storage space. System software must be highly optimized to operate efficiently within these constraints.
- Hardware Specificity: Embedded systems often use specialized hardware components that require custom device drivers and system software. The system software must be tailored to the specific hardware configuration of the device.
- Reliability and Safety: Embedded systems are often used in critical applications where failures can have serious consequences. System software must be designed to be highly reliable and safe, with robust error handling and fault tolerance mechanisms.
Here are some examples of system software commonly found in embedded systems:
- Real-Time Operating Systems (RTOS): RTOS are designed to meet the real-time requirements of embedded systems. They provide features such as task scheduling, interrupt handling, and resource management. Examples include FreeRTOS, QNX, and VxWorks.
- Device Drivers: Embedded systems often use specialized hardware components that require custom device drivers. These drivers allow the operating system to communicate with the hardware and control its functions.
- Firmware: Firmware is software that is embedded in the hardware of a device. It provides the basic functionality for the device to operate, such as boot-up procedures, hardware initialization, and device-specific functions.
User Interaction with System Software
System software, the backbone of any computer system, provides a platform for users to interact with hardware and execute applications. User interaction with system software is facilitated through various interfaces, each offering a distinct approach and user experience.
Graphical User Interfaces (GUIs)
GUIs are visually appealing and intuitive interfaces that use graphical elements such as icons, menus, and windows to represent system functions and data. They provide a user-friendly approach, making system software accessible to a wider range of users, including those with limited technical expertise.
- Ease of Use: GUIs offer a simple and intuitive way to interact with system software, eliminating the need for complex commands or syntax. Users can navigate through menus, click on icons, and drag-and-drop files, simplifying tasks like file management, application launching, and system configuration.
- Visual Feedback: GUIs provide visual feedback to users, making it easier to understand the system’s state and the results of actions. For example, a progress bar visually indicates the progress of a task, while icons and color-coding help identify different files and folders.
- User-Friendly Navigation: GUIs use familiar metaphors and visual cues, making it easier for users to navigate through different system functions and settings. For instance, the use of folders and files to represent data organization is a familiar concept that makes file management intuitive.
Command-Line Interfaces (CLIs)
CLIs are text-based interfaces that rely on commands entered by the user to interact with system software. They offer a more direct and powerful way to control system functions, providing access to advanced features and options not available through GUIs.
- Direct Control: CLIs offer a direct and powerful way to interact with system software, allowing users to execute commands with precision and flexibility. This is particularly useful for tasks that require specific parameters or configurations, such as system administration or scripting.
- Efficiency: CLIs can be more efficient than GUIs for repetitive tasks or complex operations. Users can create scripts or aliases to automate tasks, reducing the need for manual interaction.
- Advanced Functionality: CLIs provide access to a wider range of system functions and options, including low-level system configuration and debugging tools.
User Experience
The user experience of interacting with system software depends on the specific application and the interface used. GUIs generally provide a more user-friendly and accessible experience, making them suitable for a wide range of users. However, CLIs offer a more powerful and efficient way to interact with system software, making them ideal for advanced users and specific tasks.
Future Directions in System Software
The field of system software is constantly evolving, driven by advancements in hardware, software development methodologies, and emerging technologies. As we move forward, the role of system software will become increasingly critical in shaping the future of computing.
Impact of Emerging Technologies
Emerging technologies like quantum computing and blockchain are poised to revolutionize system software development.
- Quantum computing, with its ability to perform computations at speeds far exceeding classical computers, will require new system software paradigms. Quantum operating systems, programming languages, and libraries will be essential for harnessing the power of quantum processors.
- Blockchain technology, known for its decentralized and secure nature, will impact system software in areas like distributed computing, data storage, and security. Blockchain-based operating systems and applications will enable secure and transparent data management and collaboration.
Future Trends in System Software
Several key trends will shape the future of system software:
- Enhanced security: System software will play a crucial role in protecting against evolving cyber threats. Advanced security features, including intrusion detection, malware prevention, and data encryption, will be integrated into system software to ensure robust security.
- Improved performance: As hardware becomes more powerful, system software will need to optimize performance to fully utilize these capabilities. Techniques like parallel processing, caching, and resource management will be refined to enhance system performance.
- Greater integration with other technologies: System software will increasingly integrate with other technologies, such as artificial intelligence (AI), cloud computing, and the Internet of Things (IoT). This integration will enable new applications and functionalities, enhancing the user experience.
Challenges and Opportunities
The future of system software presents both challenges and opportunities:
- Developing system software for quantum computers is a significant challenge, requiring new algorithms, programming models, and debugging tools. However, this challenge also presents an opportunity to explore new computational paradigms and unlock unprecedented computing power.
- Integrating blockchain technology into system software requires addressing issues like scalability, performance, and interoperability. However, this integration offers the potential to create more secure, transparent, and decentralized systems.
- The increasing complexity of system software makes it difficult to ensure reliability and maintainability. Developers need to adopt new methodologies and tools to manage this complexity, ensuring software quality and security.
Final Wrap-Up
As technology continues to evolve, system software remains at the forefront of innovation, adapting to emerging trends and shaping the future of computing. From cloud computing to artificial intelligence, system software plays a crucial role in harnessing the power of these advancements, enabling us to explore new frontiers in the digital realm.
System software, like an operating system, provides the foundation for applications to run smoothly. One such application is autocad drawing , a powerful tool for creating detailed and precise designs. While AutoCAD relies on system software for its operation, it also contributes to the overall functionality of the computer by utilizing its resources to execute complex drawing tasks.

