Softether VPN is a powerful and versatile VPN solution that offers a wide range of features and benefits for both individuals and organizations. Developed by the Softether VPN Project, it has gained popularity for its robust security, user-friendly interface, and extensive customization options. This comprehensive guide delves into the intricacies of Softether VPN, exploring its history, technical aspects, configurations, use cases, advantages, disadvantages, community, and future prospects. We’ll also discuss security best practices, legal considerations, and address frequently asked questions.
Table of Contents
From establishing secure remote access to enhancing online privacy and circumventing censorship, Softether VPN provides a reliable and flexible solution for various digital needs. Its open-source nature and active community foster innovation and ongoing development, ensuring its relevance in the ever-evolving landscape of VPN technology.
Softether VPN
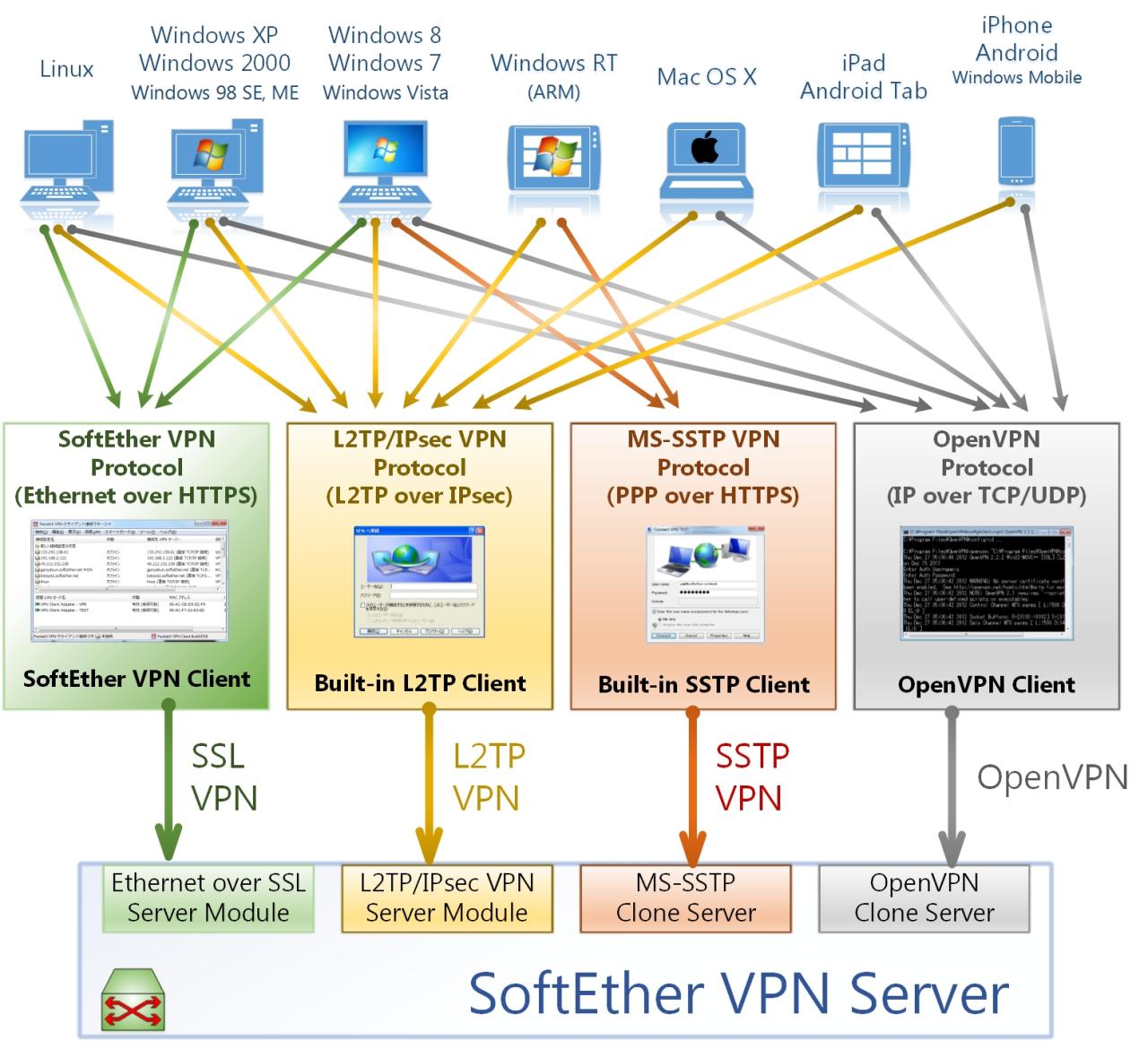
Softether VPN is a free and open-source VPN software that offers a wide range of features and functionalities for secure and private internet access. It is known for its flexibility, customization options, and support for various VPN protocols.
History and Development
Softether VPN was developed by the University of Tsukuba in Japan. Its development began in 2004, with the first version released in 2005. Since then, it has undergone numerous updates and improvements, adding new features and enhancing existing ones. The software’s development is driven by a community of developers and users who contribute to its ongoing maintenance and evolution.
Key Features and Benefits
Softether VPN provides a comprehensive set of features that cater to various needs and use cases. Here are some of its key features and benefits:
VPN Protocols
Softether VPN supports a wide range of VPN protocols, including:
- L2TP/IPsec
- OpenVPN
- PPTP
- SSTP
- IKEv2
This wide protocol support allows users to choose the most appropriate protocol for their specific needs and security requirements.
Virtual Hubs
Softether VPN allows users to create virtual hubs, which act as central points for connecting multiple devices and networks. This feature enables users to establish secure and private connections between different locations, even across geographically dispersed networks.
Multi-hop VPN
Softether VPN supports multi-hop VPN connections, which route traffic through multiple VPN servers. This adds an extra layer of security by obscuring the user’s IP address and making it more difficult for attackers to track their online activities.
Remote Access
Softether VPN provides remote access capabilities, allowing users to connect to their home or office network securely from any location. This feature is particularly useful for employees who need to access company resources remotely or for individuals who want to manage their home network from a distance.
Customization
Softether VPN offers a high degree of customization, allowing users to configure various settings to suit their specific needs. This includes options for setting up VPN servers, configuring firewall rules, and managing user accounts.
Open Source
Softether VPN is open-source software, meaning its source code is freely available for inspection and modification. This transparency allows users to verify the software’s security and functionality and encourages community involvement in its development.
Technical Aspects of Softether VPN
Softether VPN is a versatile and feature-rich VPN solution that offers a wide range of capabilities for secure network connectivity. Its technical foundation lies in a combination of established and innovative technologies, designed to provide robust security and flexibility for users.
Virtual Private Networks (VPNs)
VPNs are essential tools for enhancing data security and privacy in today’s interconnected world. They establish secure, encrypted connections between devices and networks, effectively masking the user’s location and protecting sensitive information from interception. This is achieved by creating a virtual tunnel over a public network, such as the internet, encapsulating data packets within an encrypted layer.
Technology and Protocols
Softether VPN leverages a combination of protocols and technologies to provide secure and reliable VPN services.
- IPsec (Internet Protocol Security): A widely adopted suite of protocols that provides authentication and encryption for IP-based communication. IPsec is often used in conjunction with other VPN protocols to enhance security.
- OpenVPN: A popular open-source VPN protocol known for its robust security and flexibility. Softether VPN supports OpenVPN, enabling users to connect to OpenVPN-based servers.
- L2TP/IPsec (Layer 2 Tunneling Protocol/IPsec): A combination of protocols that establishes a secure tunnel over a public network, offering strong encryption and authentication.
- SSL VPN (Secure Sockets Layer VPN): A type of VPN that utilizes the SSL/TLS protocol to create a secure connection between a client and a server. SSL VPNs are often used for remote access to corporate networks.
- SoftEther VPN Protocol: Softether VPN’s proprietary protocol, designed to provide high performance and advanced features, including multi-hop VPNs and virtual hub functionality.
Security Mechanisms
Softether VPN employs a variety of security mechanisms to protect user data and ensure secure communication.
- Encryption: Softether VPN uses strong encryption algorithms, such as AES-256, to encrypt data transmitted over the VPN tunnel, making it virtually unreadable to unauthorized parties.
- Authentication: To ensure that only authorized users can access the VPN, Softether VPN supports various authentication methods, including passwords, certificates, and multi-factor authentication.
- Firewall: Softether VPN includes a built-in firewall that helps to protect the VPN server and client devices from unauthorized access and malicious attacks.
- Anti-Malware: Softether VPN can be integrated with anti-malware software to detect and prevent malware from entering the VPN tunnel.
- VPN Server Security: Softether VPN offers advanced security features for VPN servers, such as secure boot, anti-tampering, and intrusion detection systems, to prevent unauthorized access and compromise.
Softether VPN Use Cases and Applications
Softether VPN, with its versatility and robust features, offers a wide range of applications for individuals and organizations alike. Its ability to create secure connections across diverse networks and devices makes it a valuable tool for various scenarios, from remote access to enhancing online privacy.
Remote Access
Remote access is one of the most common use cases for Softether VPN. It enables users to securely connect to their office networks or home computers from anywhere in the world. This is particularly useful for employees who work remotely, travelers who need to access company resources, or individuals who want to manage their home computers while away.
- Secure Connection: Softether VPN encrypts all data transmitted between the user’s device and the remote network, ensuring that sensitive information remains protected from unauthorized access.
- Remote Desktop Access: Users can access their desktop computers remotely, allowing them to work on files, run applications, and manage their systems as if they were physically present.
- Remote File Transfer: Softether VPN facilitates secure file sharing between devices, enabling users to transfer documents, media, and other files between their remote and local computers.
Online Privacy
Softether VPN provides a robust solution for enhancing online privacy. It masks the user’s IP address, making it difficult for websites and online trackers to identify their location and browsing activities.
- IP Address Masking: Softether VPN routes internet traffic through its servers, effectively hiding the user’s real IP address and making it appear as if they are browsing from a different location.
- Data Encryption: All data transmitted through Softether VPN is encrypted, protecting sensitive information from being intercepted by third parties.
- Bypass Geo-Restrictions: Softether VPN allows users to bypass geo-restrictions imposed by websites and streaming services, enabling them to access content that is not available in their region.
Secure Communication
Softether VPN enables secure communication between different devices and networks, ensuring that sensitive information is protected from eavesdropping and unauthorized access.
- Encrypted Messaging: Softether VPN can be used to establish secure communication channels for instant messaging and email, ensuring that messages are encrypted and protected from interception.
- Secure File Sharing: Softether VPN facilitates secure file sharing between devices, ensuring that files are encrypted during transmission and protected from unauthorized access.
- Secure Voice and Video Calls: Softether VPN can be used to establish secure voice and video call connections, protecting conversations from eavesdropping.
Real-World Examples
- Businesses: Many businesses use Softether VPN to enable remote access for employees, secure communication between offices, and protect sensitive data. Examples include small businesses, multinational corporations, and government agencies.
- Individuals: Individuals use Softether VPN for various purposes, including online privacy, bypassing geo-restrictions, and accessing content that is blocked in their region.
- Non-profit Organizations: Non-profit organizations often use Softether VPN to secure communication and data, especially when working in sensitive environments or with sensitive information.
Future Developments and Trends in VPN Technology: Softether

The world of VPN technology is constantly evolving, driven by increasing user demand for privacy, security, and access to geographically restricted content. Softether VPN, with its robust features and open-source nature, is well-positioned to adapt to these evolving trends and maintain its competitive edge.
Emerging Trends and Their Impact on Softether VPN
The rapid advancements in technology are shaping the future of VPNs, presenting both opportunities and challenges for Softether VPN.
- Increased Use of Mobile Devices: The proliferation of smartphones and tablets has led to a surge in mobile VPN usage. Softether VPN can leverage its cross-platform compatibility and lightweight nature to cater to this growing demand.
- Cloud-Based VPNs: Cloud computing has revolutionized VPN deployment, enabling more flexible and scalable solutions. Softether VPN can integrate with cloud platforms like AWS and Azure to offer a seamless cloud-based VPN experience.
- Focus on Privacy and Security: User concerns about data privacy and online security are driving the adoption of advanced encryption protocols and privacy-focused VPN services. Softether VPN, with its strong encryption algorithms and open-source nature, can capitalize on this trend.
Future Directions and Advancements in VPN Technology, Softether
The future of VPN technology holds exciting advancements that can enhance user experience and security.
- Zero-Trust Security: This emerging security paradigm assumes that no user or device can be trusted by default, requiring continuous verification and authorization. Softether VPN can integrate zero-trust principles to enhance its security posture.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML can be leveraged to detect and mitigate threats, optimize VPN performance, and personalize user experience. Softether VPN can incorporate AI/ML algorithms to enhance its functionality and security.
- Next-Generation VPN Protocols: New VPN protocols, like WireGuard, are emerging with improved performance and security features. Softether VPN can explore and integrate these protocols to enhance its capabilities.
Challenges and Opportunities for Softether VPN
The evolving technological landscape presents both challenges and opportunities for Softether VPN.
- Competition from Commercial VPN Providers: The VPN market is becoming increasingly competitive, with numerous commercial providers offering a wide range of features and pricing plans. Softether VPN needs to differentiate itself by highlighting its open-source nature, flexibility, and customizability.
- Regulation and Legal Challenges: Governments worldwide are increasingly regulating VPNs, posing challenges to their operation and privacy. Softether VPN needs to navigate these regulations and ensure compliance while protecting user privacy.
- Maintaining Security and Stability: The ever-evolving threat landscape necessitates constant vigilance and updates to maintain security and stability. Softether VPN needs to invest in research and development to stay ahead of emerging threats and vulnerabilities.
Last Word
Understanding the intricacies of Softether VPN empowers users to make informed decisions about their online security and privacy. Whether you’re a tech-savvy individual seeking enhanced protection or an organization seeking robust remote access solutions, Softether VPN offers a compelling choice. Its combination of security, flexibility, and community support makes it a valuable tool for navigating the complexities of the digital world. By exploring the various aspects of Softether VPN, we gain a deeper appreciation for its capabilities and its potential to enhance our digital lives.
Softether VPN is a powerful tool for establishing secure connections, particularly useful for remote access and bypassing geographical restrictions. While it excels in networking, it might not be the ideal choice for opening PDF files, which is where a dedicated solution like adobe reader online comes in handy.
Softether’s focus on security and reliability makes it a great complement to Adobe Reader, ensuring a seamless experience for accessing and managing sensitive documents.

