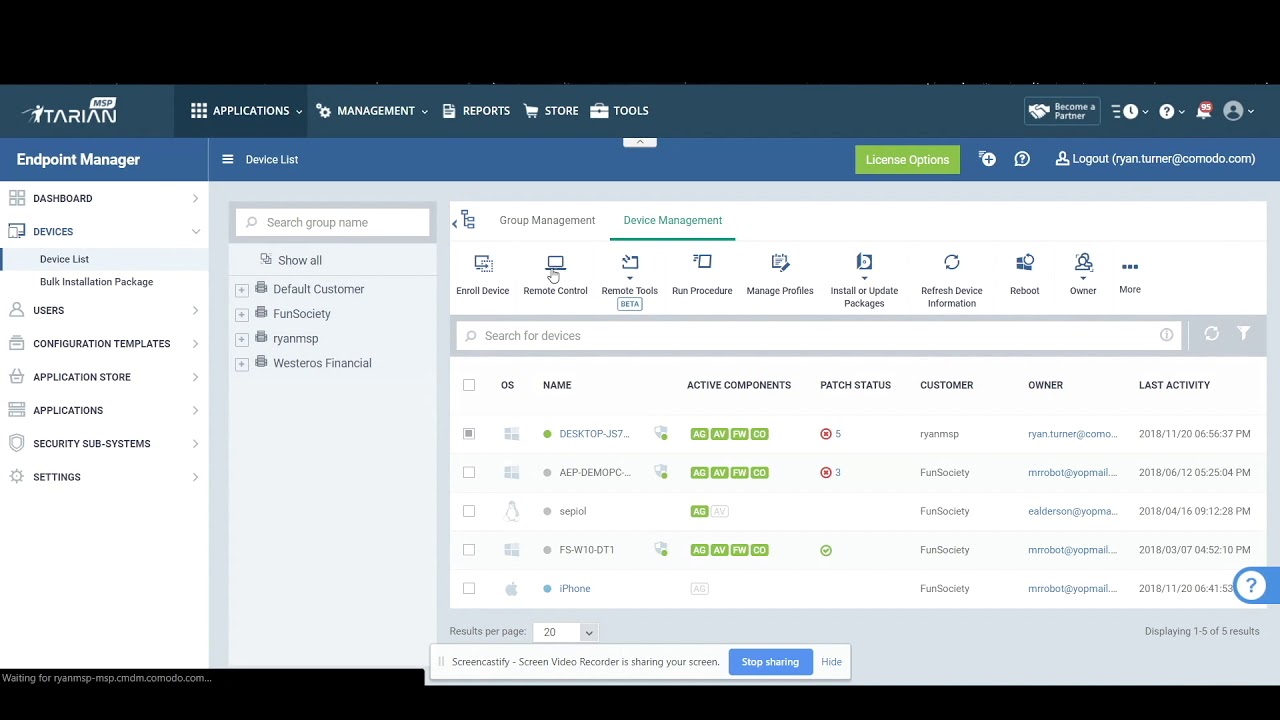
Remote monitoring management software sets the stage for a seamless and efficient approach to managing IT infrastructure, providing a real-time view of systems and applications, and ensuring optimal performance. From proactively identifying and resolving issues to enhancing security and compliance, this software empowers organizations to achieve their business objectives.
Table of Contents
The software utilizes various technologies and techniques to monitor and manage diverse aspects of IT infrastructure, including network connectivity, server performance, application health, and security threats. This comprehensive approach enables organizations to gain valuable insights into their systems, identify potential problems before they escalate, and optimize resource utilization.
Incident Response and Resolution
Remote monitoring management software plays a crucial role in streamlining incident response and resolution, enabling organizations to quickly identify, analyze, and address security threats and system issues. This software automates various processes, reducing manual effort and improving efficiency.
Automated Incident Notification and Escalation
Automated incident notification and escalation are critical components of effective incident response. This feature ensures that relevant personnel are promptly alerted about security incidents or system failures. When a system anomaly or security threat is detected, the software automatically generates alerts and escalates them to designated teams or individuals based on predefined rules and escalation paths. This prompt notification helps to minimize downtime and mitigate potential damage.
- Email notifications: The software can send email alerts to individuals or teams, providing details about the incident, including the time of occurrence, affected systems, and initial assessment. This ensures that stakeholders are immediately informed and can take appropriate actions.
- SMS notifications: For critical incidents requiring immediate attention, the software can send SMS alerts to key personnel, ensuring they are notified even when they are away from their computers.
- Push notifications: The software can send push notifications to mobile devices, allowing users to receive real-time updates about incidents and take action quickly, regardless of their location.
- Automated escalation: If an incident is not resolved within a specified timeframe, the software can automatically escalate it to higher-level personnel or teams, ensuring that the issue receives the necessary attention and resources.
Root Cause Analysis and Troubleshooting
Remote monitoring management software provides comprehensive tools for root cause analysis and troubleshooting, helping organizations understand the underlying causes of incidents and resolve them effectively.
- Log analysis: The software can analyze system logs to identify patterns and anomalies that may indicate security threats or system failures. This analysis helps to pinpoint the root cause of the incident and identify the affected components.
- Real-time monitoring: By continuously monitoring system performance and security metrics, the software can detect issues in real time, enabling early intervention and preventing escalation.
- Performance dashboards: The software provides interactive dashboards that display key performance indicators (KPIs) and system metrics, allowing administrators to quickly identify potential issues and investigate further.
- Correlation engine: The software can correlate data from multiple sources, such as logs, security alerts, and performance metrics, to identify complex relationships and pinpoint the root cause of incidents.
Incident Documentation and Reporting
Proper incident documentation and reporting are essential for improving incident response processes and identifying areas for improvement. Remote monitoring management software provides tools for capturing detailed information about incidents and generating comprehensive reports.
- Incident tickets: The software allows administrators to create and manage incident tickets, capturing details such as the incident description, affected systems, resolution steps, and time spent on resolution.
- Reporting capabilities: The software generates reports that provide insights into incident trends, frequency, and resolution times. This information helps organizations identify common issues, assess the effectiveness of their incident response processes, and prioritize security improvements.
- Customizable reporting: The software allows users to create custom reports that focus on specific areas of interest, such as security threats, system performance, or user behavior.
Remediation and Recovery Actions
Remote monitoring management software facilitates remediation and recovery actions, enabling organizations to quickly restore systems to their operational state after incidents.
- Automated remediation: For certain types of incidents, the software can automatically apply pre-defined remediation actions, such as restarting services, applying security patches, or isolating affected systems.
- Automated recovery: The software can automate the recovery of systems from backups, ensuring minimal downtime and data loss.
- Incident response playbooks: The software allows organizations to create and manage incident response playbooks, which Artikel the steps to be taken in response to specific incidents. These playbooks provide a structured approach to incident response, ensuring consistency and efficiency.
Security and Compliance

Remote monitoring management software plays a crucial role in securing and managing IT infrastructure, but it also introduces unique security and compliance considerations. Implementing robust security measures and adhering to relevant regulations is essential to protect sensitive data and maintain operational integrity.
Data Encryption and Security Protocols
Data encryption and security protocols are essential for protecting sensitive information transmitted and stored by remote monitoring management software.
- Data Encryption: Data encryption ensures that information is scrambled and unreadable to unauthorized parties. Remote monitoring management software should utilize strong encryption algorithms, such as AES-256, to encrypt data both in transit and at rest. This protects data from interception and unauthorized access.
- Secure Communication Protocols: Secure communication protocols, such as TLS/SSL, are crucial for protecting data transmitted between the software and managed devices. These protocols establish secure connections that encrypt data, preventing eavesdropping and tampering.
Access Control and User Authentication
Access control and user authentication mechanisms are essential for restricting access to the remote monitoring management software and its data to authorized personnel.
- Role-Based Access Control: Implementing role-based access control (RBAC) ensures that users only have access to the information and functionalities they require. This helps prevent unauthorized access and maintain data integrity.
- Multi-Factor Authentication: Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile device. This makes it significantly harder for unauthorized individuals to gain access.
- Strong Password Policies: Enforcing strong password policies, such as requiring a minimum length, a combination of uppercase and lowercase letters, numbers, and special characters, and regular password changes, can help prevent unauthorized access through brute-force attacks.
Compliance with Industry Regulations and Standards, Remote monitoring management software
Remote monitoring management software must comply with industry regulations and standards to ensure data privacy, security, and operational integrity.
- General Data Protection Regulation (GDPR): If the software handles personal data of individuals in the European Union, it must comply with GDPR’s stringent data protection requirements, including data minimization, consent, and the right to erasure.
- Health Insurance Portability and Accountability Act (HIPAA): Organizations in the healthcare industry must comply with HIPAA regulations, which require secure handling and storage of protected health information (PHI).
- Payment Card Industry Data Security Standard (PCI DSS): Businesses handling credit card information must comply with PCI DSS, which sets standards for securing cardholder data and preventing fraud.
Vulnerability Management and Patching
Vulnerability management and patching are critical for addressing security vulnerabilities in the remote monitoring management software and its underlying infrastructure.
- Regular Vulnerability Scanning: Regular vulnerability scanning helps identify potential weaknesses and vulnerabilities in the software and its components.
- Prompt Patching: Promptly applying security patches and updates is essential for addressing known vulnerabilities and preventing exploitation by attackers.
- Security Information and Event Management (SIEM): Implementing a SIEM system can help detect and respond to security incidents by correlating and analyzing security events from various sources.
Closing Notes: Remote Monitoring Management Software
In conclusion, remote monitoring management software is a powerful tool that empowers organizations to achieve a higher level of IT efficiency and security. By leveraging its capabilities, businesses can streamline operations, reduce downtime, and improve overall system performance. With the increasing complexity of modern IT environments, this software is becoming an essential component of any successful IT strategy.
Remote monitoring management software empowers businesses to stay on top of their operations, even when they’re not physically present. One solution that excels in this area is uniflow , which offers comprehensive monitoring and management capabilities, allowing you to track key performance indicators, receive real-time alerts, and remotely control devices.
With such software, businesses can optimize their workflows, reduce downtime, and improve overall efficiency.