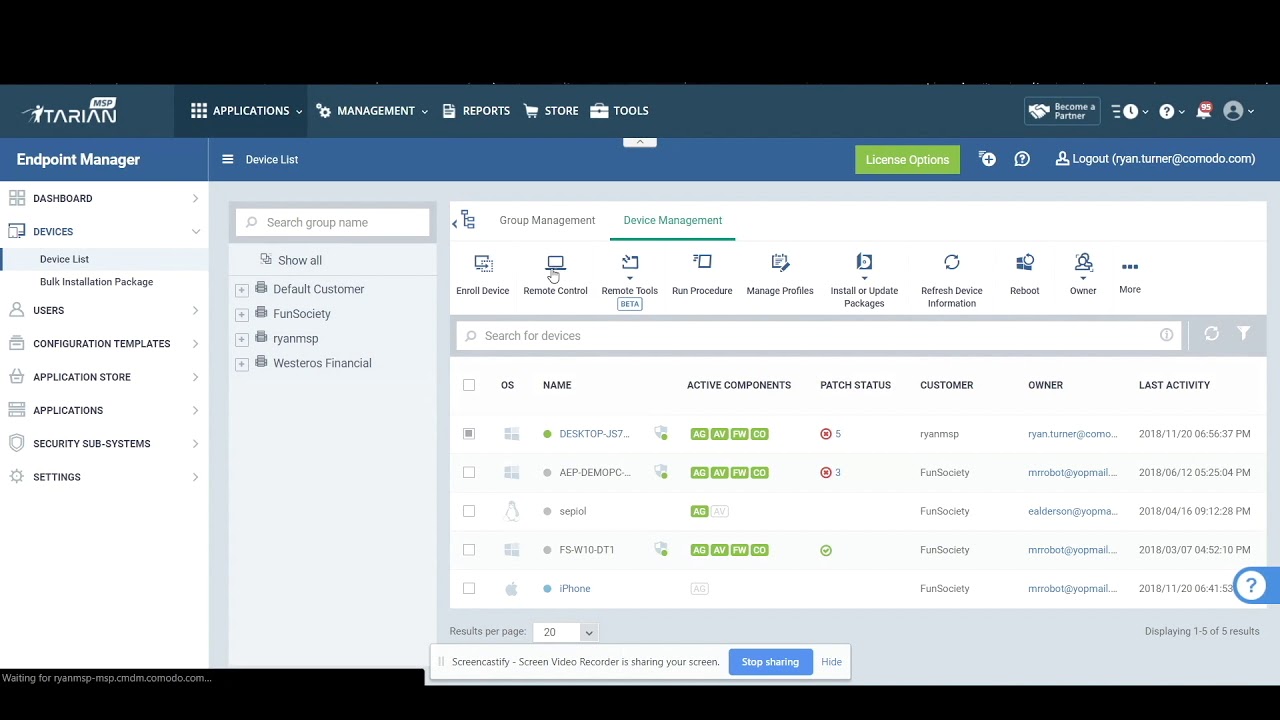
Remote monitoring and management platforms have revolutionized the way businesses manage their IT infrastructure. These powerful tools provide a centralized hub for monitoring, managing, and securing devices across an entire network, offering unparalleled control and visibility.
Table of Contents
From automating routine tasks to proactively identifying and resolving issues, RMM platforms empower IT professionals to optimize performance, enhance security, and streamline operations. This comprehensive guide delves into the key features, benefits, and considerations for implementing an RMM platform, equipping businesses with the knowledge to make informed decisions and unlock the full potential of these transformative technologies.
Introduction to Remote Monitoring and Management (RMM) Platforms
Remote monitoring and management (RMM) platforms are software solutions that allow IT professionals to remotely manage and monitor computer systems, networks, and devices. They provide a centralized platform for managing IT infrastructure, streamlining tasks, and enhancing security.
RMM platforms have become essential tools for businesses of all sizes, enabling them to optimize IT operations, improve efficiency, and minimize downtime.
Key Features and Functionalities of RMM Platforms
RMM platforms offer a wide range of features and functionalities to address various IT management needs.
- Remote Access and Control: RMM platforms provide secure remote access to devices, allowing IT professionals to troubleshoot issues, install software, and perform other administrative tasks remotely. This capability significantly reduces the need for on-site visits, saving time and resources.
- System Monitoring: RMM platforms continuously monitor critical system parameters such as CPU utilization, memory usage, disk space, and network performance. This real-time monitoring helps identify potential issues before they escalate into major problems, preventing downtime and ensuring system stability.
- Patch Management: Keeping software and operating systems updated with the latest security patches is crucial for protecting against vulnerabilities. RMM platforms automate the patch management process, ensuring all devices are up-to-date and secure.
- Endpoint Security: RMM platforms provide comprehensive endpoint security features, including antivirus protection, firewall management, and intrusion detection. They help prevent malware infections, data breaches, and other security threats.
- Reporting and Analytics: RMM platforms generate detailed reports and analytics on system performance, security threats, and user activity. These insights provide valuable data for optimizing IT operations, identifying areas for improvement, and making informed decisions.
- Ticket Management: RMM platforms often include integrated ticketing systems that allow users to submit support requests and track their progress. This streamlined approach helps manage IT support requests efficiently and improves communication between IT staff and users.
Benefits of Utilizing RMM Platforms for Businesses
RMM platforms offer numerous benefits for businesses, including:
- Improved IT Efficiency: RMM platforms automate routine IT tasks, freeing up IT staff to focus on more strategic initiatives. This increased efficiency translates into cost savings and improved productivity.
- Enhanced Security: RMM platforms provide comprehensive security features that protect against cyber threats and data breaches. This is particularly important in today’s digital landscape, where security breaches are becoming increasingly common.
- Reduced Downtime: RMM platforms proactively monitor systems and identify potential issues before they lead to downtime. This minimizes disruptions to business operations and ensures continuous productivity.
- Centralized Management: RMM platforms provide a single platform for managing all IT assets, simplifying administration and reducing complexity. This centralized approach makes it easier to monitor, manage, and secure the entire IT infrastructure.
- Improved Customer Support: RMM platforms can help businesses provide faster and more efficient customer support. By remotely accessing devices and troubleshooting issues, IT staff can resolve problems quickly and minimize downtime for users.
- Cost Savings: RMM platforms can help businesses save money by reducing the need for on-site IT support, minimizing downtime, and improving efficiency. These cost savings can be significant, especially for businesses with large IT infrastructures.
Essential Components of an RMM Platform
A robust Remote Monitoring and Management (RMM) platform consists of several core components that work together to provide comprehensive management and security for IT systems. These components are designed to automate tasks, improve efficiency, and ensure the smooth operation of your network and devices.
Remote Access
Remote access is a fundamental feature of any RMM platform, allowing technicians to connect to and control remote devices securely. This capability is crucial for troubleshooting issues, installing software, and performing other administrative tasks without physically being present at the device’s location.
- Secure Connections: RMM platforms employ encryption protocols like Secure Shell (SSH) and Secure Socket Layer (SSL) to protect data during remote sessions, ensuring confidentiality and integrity.
- Multi-Factor Authentication: Many RMM platforms implement multi-factor authentication (MFA) for an extra layer of security, requiring users to provide multiple forms of identification before granting access.
- Session Recording and Auditing: Some platforms record remote sessions for auditing purposes, allowing administrators to track activity and ensure compliance with security policies.
System Monitoring
System monitoring is essential for identifying potential problems before they impact users or disrupt operations. RMM platforms provide real-time insights into the health and performance of devices and networks.
- Performance Metrics: RMM platforms track key performance indicators (KPIs) such as CPU utilization, memory usage, disk space, and network bandwidth. These metrics provide valuable information about the overall system health and potential bottlenecks.
- Event Logging and Alerts: RMM platforms capture system events and generate alerts based on predefined thresholds. This enables proactive problem detection and timely intervention, reducing downtime and improving responsiveness.
- Resource Utilization: RMM platforms can monitor resource utilization across the network, helping administrators identify potential overloads and optimize resource allocation for improved performance.
Patch Management
Patch management is crucial for maintaining the security of your IT infrastructure. RMM platforms automate the process of applying software updates and security patches to devices, reducing the risk of vulnerabilities and cyberattacks.
- Automated Patch Deployment: RMM platforms can scan devices for missing patches, download and install updates automatically, and schedule patch deployments for optimal efficiency.
- Vulnerability Scanning: RMM platforms often include vulnerability scanning capabilities to identify security weaknesses and prioritize patch deployment based on severity levels.
- Compliance Reporting: RMM platforms can generate reports detailing patch compliance across your network, ensuring that devices meet security standards and regulatory requirements.
Table of RMM Platform Components and Functionalities
| Component | Functionality |
|---|---|
| Remote Access | Securely connect to and control remote devices |
| System Monitoring | Track system health, performance, and resource utilization |
| Patch Management | Automate software updates and security patch deployment |
| Asset Management | Inventory and track hardware and software assets |
| Security Monitoring | Detect and respond to security threats and incidents |
| Reporting and Analytics | Generate reports and analyze data for insights and decision-making |
| Automation and Scripting | Automate routine tasks and implement custom solutions |
Benefits of Implementing an RMM Platform
Implementing an RMM platform offers significant advantages for organizations of all sizes. It streamlines IT management, improves security, and optimizes resource allocation, ultimately contributing to improved efficiency and reduced costs.
Enhanced Security
RMM platforms play a crucial role in enhancing security by proactively identifying and mitigating potential threats.
- Vulnerability Scanning: RMM platforms regularly scan devices for vulnerabilities, ensuring that security patches are applied promptly. This minimizes the risk of exploitation by malicious actors.
- Endpoint Security: RMM platforms offer centralized management of endpoint security measures, including antivirus software, firewall configurations, and intrusion detection systems. This provides a comprehensive approach to safeguarding devices against malware and other threats.
- Real-time Monitoring: RMM platforms monitor network activity and device behavior in real-time, enabling the detection of suspicious activity or anomalies. This allows for immediate intervention to prevent data breaches or other security incidents.
Improved Efficiency
RMM platforms automate routine tasks and processes, freeing up IT staff to focus on more strategic initiatives.
- Automated Patching: RMM platforms automate the process of patching operating systems and software applications, ensuring that systems are kept up-to-date and secure. This eliminates the need for manual patching, which can be time-consuming and error-prone.
- Remote Device Management: RMM platforms enable IT staff to manage and troubleshoot devices remotely, regardless of location. This reduces the need for on-site visits, saving time and resources.
- Centralized Reporting: RMM platforms provide comprehensive reports on device health, security status, and network performance. This enables IT staff to make informed decisions about resource allocation and system optimization.
Reduced Costs
RMM platforms can significantly reduce IT operating costs by streamlining processes, improving efficiency, and preventing costly downtime.
- Reduced Help Desk Calls: RMM platforms can automate common help desk requests, such as password resets and software installations, reducing the workload on IT support staff. This frees up their time to address more complex issues.
- Proactive Maintenance: RMM platforms allow for proactive maintenance and troubleshooting, preventing minor issues from escalating into major problems. This reduces the likelihood of costly downtime and repairs.
- Optimized Resource Allocation: RMM platforms provide real-time insights into resource utilization, enabling IT staff to optimize resource allocation and reduce unnecessary spending.
Impact on IT Support Teams
RMM platforms significantly impact IT support teams by automating routine tasks and providing real-time insights into device health and security status.
- Increased Productivity: By automating routine tasks, RMM platforms free up IT support teams to focus on more strategic initiatives, such as network optimization and security improvements.
- Improved Response Times: RMM platforms enable IT support teams to quickly identify and resolve issues remotely, reducing the time it takes to address problems.
- Enhanced Collaboration: RMM platforms provide a centralized platform for communication and collaboration among IT support team members, improving efficiency and communication.
Types of RMM Platforms Available
RMM platforms come in various forms, each catering to specific needs and budgets. Understanding the different types of RMM platforms available is crucial for choosing the right solution for your organization.
Categorization of RMM Platforms
RMM platforms can be categorized based on their target audience and features. Here are the most common types:
- Small and Medium Businesses (SMBs): These platforms offer a simplified approach to RMM, focusing on essential features like remote access, patch management, and basic monitoring. They are typically cloud-based and cost-effective, making them ideal for businesses with limited IT resources.
- Managed Service Providers (MSPs): MSP-focused RMM platforms offer comprehensive features, including advanced automation, scripting, reporting, and multi-tenant management. They enable MSPs to manage multiple clients efficiently and deliver proactive IT support.
- Enterprise Solutions: Enterprise RMM platforms cater to large organizations with complex IT infrastructure. They provide advanced features like security auditing, compliance management, and integration with other enterprise systems. These platforms are typically on-premise and require significant investment.
Cloud-Based vs. On-Premise RMM Platforms, Remote monitoring and management platform
- Cloud-Based RMM Platforms: Cloud-based platforms are hosted on the provider’s servers and accessed through a web browser or mobile app. They offer several advantages, including scalability, accessibility, and lower upfront costs. However, they may require a stable internet connection and rely on the provider’s security measures.
- On-Premise RMM Platforms: On-premise platforms are installed and managed on the organization’s own servers. They provide greater control over data and security but require significant investment in hardware, software, and IT personnel.
Key Considerations for Choosing an RMM Platform
Choosing the right RMM platform requires careful consideration of various factors. Some key considerations include:
- Target Audience: Identify the specific needs of your organization, whether it’s an SMB, MSP, or enterprise.
- Features and Functionality: Determine the essential features required, such as remote access, patch management, monitoring, reporting, and automation.
- Scalability: Consider the future growth of your organization and choose a platform that can scale with your needs.
- Cost: Evaluate the pricing models and compare the total cost of ownership, including software licenses, hardware, and support.
- Security: Ensure the platform provides robust security features to protect your data and systems.
- Integration: Check for compatibility with existing IT systems and applications.
- Support: Evaluate the level of technical support and documentation provided by the vendor.
Key Features of RMM Platforms
RMM platforms are packed with features designed to streamline IT management, enhance security, and boost overall efficiency. These features can be broadly categorized into remote access, endpoint management, and security monitoring, each contributing to a comprehensive approach to IT administration.
Remote Access
Remote access capabilities are the cornerstone of RMM platforms, allowing IT professionals to connect to and manage devices remotely. This eliminates the need for physical presence, enabling quick troubleshooting, software deployment, and system updates.
- Remote Desktop Access: This feature allows IT administrators to control and view the desktop of a remote computer as if they were sitting in front of it. This enables them to troubleshoot problems, install software, or provide real-time assistance to users.
- Remote File Transfer: This feature facilitates the transfer of files between the administrator’s computer and remote devices. This is useful for deploying software updates, transferring configuration files, or retrieving data from remote systems.
- Remote Command Execution: This feature enables the execution of commands on remote devices. This is useful for tasks such as restarting services, running scripts, or managing system settings.
Endpoint Management
Endpoint management encompasses the control and management of all devices connected to a network. RMM platforms offer a comprehensive set of tools for managing endpoints, including software deployment, patch management, and device inventory.
- Software Deployment: RMM platforms automate the process of deploying software updates and applications to multiple devices simultaneously. This ensures that all devices have the latest versions of critical software, improving security and performance.
- Patch Management: This feature allows IT administrators to manage and apply security patches to all endpoints. It helps keep systems up-to-date with the latest security fixes, mitigating the risk of vulnerabilities and cyberattacks.
- Device Inventory: RMM platforms maintain an inventory of all devices connected to the network, providing detailed information about each device, including its hardware specifications, software installed, and operating system. This helps IT teams understand the IT landscape and identify potential risks.
Security Monitoring
Security monitoring is a critical aspect of RMM platforms, ensuring that systems are protected from threats and vulnerabilities. RMM platforms provide real-time insights into security events, enabling proactive threat detection and response.
- Real-Time Threat Detection: RMM platforms continuously monitor endpoints for suspicious activity and malware infections. They use various security technologies, such as antivirus software, intrusion detection systems, and firewalls, to detect and block threats.
- Vulnerability Scanning: This feature identifies security vulnerabilities on endpoints and helps prioritize remediation efforts. By proactively addressing vulnerabilities, IT teams can reduce the risk of successful cyberattacks.
- Security Reporting: RMM platforms generate detailed reports on security events, vulnerabilities, and threats. These reports provide valuable insights into the security posture of the network and help IT teams make informed decisions about security measures.
Benefits and Drawbacks of RMM Platform Features
| Feature | Benefits | Drawbacks |
|---|---|---|
| Remote Access |
|
|
| Endpoint Management |
|
|
| Security Monitoring |
|
|
Addressing Common IT Challenges
RMM platform features can be effectively used to address common IT challenges faced by organizations:
- Slow Performance: RMM platforms can identify performance bottlenecks, such as resource-intensive applications or hardware issues, through monitoring and performance analysis. They can also automate software updates and patch management to optimize system performance.
- Security Breaches: RMM platforms provide real-time threat detection, vulnerability scanning, and security reporting, helping to identify and mitigate security threats. They also enable quick response to security incidents, minimizing the impact of attacks.
- Software Deployment: RMM platforms automate the process of deploying software updates and applications to multiple devices simultaneously. This ensures that all devices have the latest versions of critical software, improving security and performance.
- User Support: Remote access capabilities allow IT professionals to provide remote assistance to users, resolving issues quickly and efficiently. This reduces the need for onsite visits and improves user satisfaction.
Integration and Compatibility of RMM Platforms
In today’s complex IT landscape, effective management relies on seamless integration between various tools and systems. RMM platforms play a crucial role in this interconnected ecosystem, facilitating the exchange of information and automation across different applications.
Integration with Security Solutions
RMM platforms can significantly enhance security posture by integrating with existing security solutions, enabling a comprehensive approach to threat detection and response.
- Endpoint Detection and Response (EDR): Integration with EDR solutions allows RMM platforms to receive real-time threat alerts, initiate remediation actions, and isolate infected systems, minimizing the impact of security incidents. For example, an RMM platform could automatically quarantine a compromised endpoint based on an alert from an EDR system.
- Security Information and Event Management (SIEM): Integration with SIEM systems enables RMM platforms to correlate security events from various sources, identify patterns, and provide actionable insights for proactive threat mitigation. This integration helps organizations gain a holistic view of their security landscape, enabling them to detect and respond to threats more effectively.
- Vulnerability Scanners: RMM platforms can integrate with vulnerability scanners to automate vulnerability assessments, prioritize remediation efforts, and ensure timely patching. This integration streamlines the patching process, reducing the attack surface and minimizing the risk of exploitation.
Integration with Ticketing Systems
RMM platforms can streamline IT support operations by integrating with ticketing systems, automating incident management and service desk processes.
- Automated Ticket Creation: When an RMM platform detects an issue, it can automatically create a ticket in the ticketing system, assigning it to the appropriate technician. This eliminates manual ticket creation, reducing errors and saving time.
- Real-Time Status Updates: RMM platforms can provide real-time status updates on tickets, allowing technicians to track progress and provide accurate information to users. This enhances transparency and communication within the IT support team.
- Ticket Resolution and Closure: Once an issue is resolved, the RMM platform can automatically update the ticket status and close it, ensuring accurate record-keeping and efficient workflow management.
Integration with Monitoring Tools
RMM platforms can leverage data from monitoring tools to gain a comprehensive view of IT infrastructure performance and health.
- Network Performance Monitoring (NPM): Integration with NPM tools allows RMM platforms to monitor network performance metrics, identify bottlenecks, and proactively address network issues before they impact users. For instance, an RMM platform could automatically trigger a notification when network latency exceeds a predefined threshold.
- Server Monitoring: Integration with server monitoring tools enables RMM platforms to track server performance, resource utilization, and system health. This allows for proactive maintenance and troubleshooting, minimizing downtime and ensuring optimal server performance.
- Application Performance Monitoring (APM): Integration with APM tools provides insights into application performance, identifying slowdowns and bottlenecks. RMM platforms can use this data to optimize application performance, enhance user experience, and ensure business continuity.
Examples of Successful Integrations
“A large financial institution implemented an RMM platform that seamlessly integrated with its existing security solutions, including EDR, SIEM, and vulnerability scanners. This integration enabled the organization to automate threat detection, response, and remediation processes, significantly improving its security posture and reducing the risk of data breaches.”
“A healthcare provider integrated its RMM platform with its ticketing system, automating incident management and service desk processes. This integration streamlined IT support operations, reduced ticket resolution time, and improved user satisfaction.”
Security Considerations for RMM Platforms: Remote Monitoring And Management Platform
Remote monitoring and management (RMM) platforms offer significant benefits for IT teams, but their reliance on remote access and data management raises crucial security considerations. Implementing robust security measures is paramount to protect sensitive data and prevent unauthorized access.
Potential Security Vulnerabilities
RMM platforms inherently involve remote access to managed devices, which presents potential security vulnerabilities. Understanding these vulnerabilities is crucial for implementing effective security measures.
- Unauthorized Access: RMM platforms rely on credentials to access managed devices. If these credentials are compromised, attackers can gain unauthorized access to sensitive data and systems. This risk is amplified if weak or default passwords are used or if credentials are stored insecurely.
- Data Breaches: RMM platforms store and transmit sensitive data, including user credentials, system configurations, and network traffic. Data breaches can occur due to vulnerabilities in the platform itself or due to inadequate security measures in the network infrastructure.
- Malware Infection: Attackers can exploit vulnerabilities in RMM platforms to inject malware into managed devices. This malware can steal data, compromise system integrity, or launch further attacks.
- Denial-of-Service Attacks: Attackers can target RMM platforms with denial-of-service (DoS) attacks, which can disrupt service availability and prevent IT teams from effectively managing devices.
Implementing Robust Security Measures
Mitigating the security risks associated with RMM platforms requires a comprehensive approach that addresses various aspects of security. Here are some essential recommendations:
- Strong Authentication: Implement multi-factor authentication (MFA) for all user accounts. This adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code, before granting access. Additionally, enforce strong password policies and regularly rotate passwords.
- Secure Network Access: Ensure all network connections to the RMM platform are encrypted using protocols like HTTPS. Use a firewall to block unauthorized access and implement intrusion detection and prevention systems (IDS/IPS) to detect and mitigate malicious activity.
- Regular Security Audits: Perform regular security audits to identify and address vulnerabilities in the RMM platform and managed devices. These audits should include vulnerability scanning, penetration testing, and security assessments.
- Data Encryption: Encrypt all sensitive data stored and transmitted by the RMM platform. This includes user credentials, system configurations, and network traffic. Use strong encryption algorithms and regularly update encryption keys.
- Access Control: Implement granular access control measures to restrict user permissions based on their roles and responsibilities. This ensures that only authorized users can access specific data and functions within the RMM platform.
- Security Awareness Training: Provide security awareness training to all users who interact with the RMM platform. This training should cover best practices for password security, data protection, and phishing prevention.
- Patch Management: Maintain a consistent patch management program for both the RMM platform and managed devices. Regularly install security patches to address vulnerabilities and mitigate risks.
- Incident Response Plan: Develop a comprehensive incident response plan to handle security incidents effectively. This plan should Artikel steps for detecting, containing, and recovering from security breaches. Regularly test and update this plan to ensure its effectiveness.
Data Security and Privacy
Data security and privacy are paramount concerns when using RMM platforms. RMM platforms often collect and store sensitive data, including user credentials, system configurations, and network traffic. It is essential to implement robust measures to protect this data and ensure compliance with data privacy regulations.
- Data Minimization: Only collect and store data that is necessary for the operation and management of the RMM platform. Avoid collecting unnecessary data, which can increase the risk of data breaches and privacy violations.
- Data Retention Policies: Establish clear data retention policies that specify how long data is stored and when it is deleted. This ensures that data is only retained for as long as necessary and is disposed of securely when no longer needed.
- Data Encryption: Encrypt all sensitive data at rest and in transit. This ensures that even if data is intercepted, it cannot be accessed without the appropriate decryption keys.
- Data Access Control: Implement granular access control measures to restrict access to sensitive data based on user roles and responsibilities. This ensures that only authorized users can access specific data.
- Compliance with Regulations: Ensure compliance with relevant data privacy regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). This involves implementing appropriate security measures and ensuring that data subjects have the necessary rights and controls over their personal data.
Case Studies and Success Stories
The effectiveness of RMM platforms is best illustrated through real-world examples of businesses that have successfully implemented them. These case studies demonstrate the challenges organizations faced, the benefits they realized, and the overall impact of RMM solutions on IT operations, efficiency, and security.
Impact of RMM on IT Operations
The adoption of RMM platforms has significantly impacted IT operations across various industries. Businesses have reported a considerable reduction in the time spent on routine tasks, enabling IT teams to focus on more strategic initiatives. For example, a mid-sized healthcare provider implemented an RMM platform to automate routine tasks such as software updates, patch management, and system backups. This freed up IT staff to focus on more complex projects like migrating to a new electronic health record (EHR) system. The result was a more efficient IT department, improved system security, and a smoother EHR migration process.
Future Trends in RMM Platforms
The realm of remote monitoring and management (RMM) platforms is constantly evolving, driven by technological advancements and the ever-changing landscape of IT management and cybersecurity. Emerging trends are shaping the future of RMM platforms, promising to enhance efficiency, security, and the overall IT experience.
Artificial Intelligence and Automation
The integration of artificial intelligence (AI) and automation is revolutionizing RMM platforms. AI algorithms can analyze vast amounts of data, identify patterns, and predict potential issues before they occur. This proactive approach to IT management allows for timely interventions, minimizing downtime and improving system stability.
- Predictive Maintenance: AI-powered RMM platforms can analyze historical data and system performance metrics to predict potential hardware failures. This allows IT teams to proactively replace components before they fail, reducing downtime and unexpected disruptions.
- Automated Patching: AI can automate the process of identifying and deploying software updates, ensuring systems are always up-to-date and protected against vulnerabilities.
- Security Threat Detection: AI algorithms can analyze network traffic and system behavior to detect suspicious activities and potential security breaches, providing real-time alerts and enabling swift response.
Closing Summary
In conclusion, remote monitoring and management platforms are essential tools for modern IT management. By providing centralized control, automation, and proactive monitoring capabilities, RMM solutions enable businesses to optimize performance, enhance security, and reduce costs. As technology continues to evolve, the role of RMM platforms will become even more critical in ensuring the smooth and efficient operation of IT infrastructure.
Remote monitoring and management platforms offer valuable insights into your network’s health, but sometimes you need a deeper level of protection. For comprehensive security, consider using a robust antivirus solution like 360 antivirus , which can help you identify and mitigate threats before they impact your systems.
This, in turn, enhances the effectiveness of your remote monitoring and management platform by ensuring a stable and secure environment for your network.