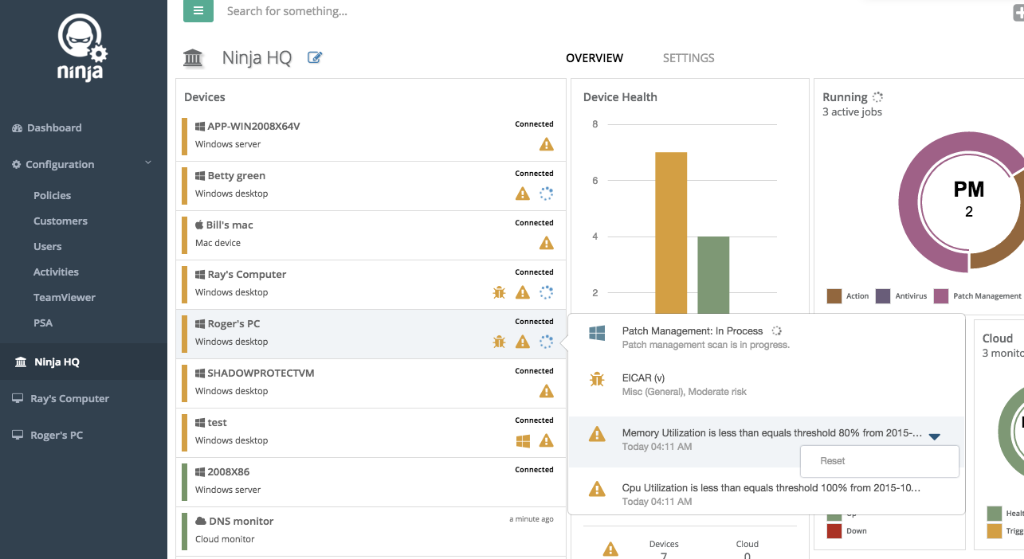
Ninja RMM Remote Access is a powerful tool that empowers IT professionals to manage and support devices remotely, enhancing efficiency and security. This comprehensive solution offers a suite of features that streamline IT operations, providing a seamless experience for both administrators and end users.
Table of Contents
Ninja RMM’s remote access capabilities are designed to address the growing need for secure and reliable connectivity in today’s hybrid work environment. By providing a secure and reliable connection, Ninja RMM enables IT teams to resolve issues quickly, minimize downtime, and optimize system performance.
Remote Access in Ninja RMM
Ninja RMM offers various remote access methods to manage and support your clients’ devices remotely. These methods cater to different needs and scenarios, providing flexibility and control over how you connect to client devices.
Remote Access Methods
Ninja RMM provides several remote access methods, each with its advantages and disadvantages.
- NinjaConnect: This method uses a secure, browser-based connection to access client devices. It’s ideal for quick, ad-hoc sessions and doesn’t require any software installation on the client device.
- Ninja Remote: This method allows you to establish a full-screen remote desktop connection, providing complete control over the client device. It requires a lightweight agent to be installed on the client device.
- TeamViewer: This third-party remote access solution can be integrated with Ninja RMM, offering advanced features like file transfer and remote printing. It requires a separate TeamViewer account and a TeamViewer agent to be installed on the client device.
- Remote Desktop Protocol (RDP): This standard protocol enables remote access to Windows devices. It can be used in conjunction with Ninja RMM for more complex remote access scenarios.
Advantages and Disadvantages of Remote Access Methods
The choice of remote access method depends on the specific situation and your needs.
| Method | Advantages | Disadvantages |
|---|---|---|
| NinjaConnect |
|
|
| Ninja Remote |
|
|
| TeamViewer |
|
|
| RDP |
|
|
Security Measures in Ninja RMM
Ninja RMM implements several security measures to protect remote access sessions.
- Two-factor authentication: Requires users to provide two forms of authentication before accessing remote sessions, enhancing account security.
- Encryption: All remote access sessions are encrypted using industry-standard protocols, ensuring data confidentiality.
- Access control: Administrators can control which users have access to specific devices and restrict their actions.
- Session logging: All remote access sessions are logged, providing an audit trail for security purposes.
- Security updates: Ninja RMM regularly releases security updates to address vulnerabilities and ensure the platform’s security.
Benefits of Using Ninja RMM for Remote Access
Ninja RMM offers a comprehensive suite of tools that can significantly streamline and enhance your remote access capabilities, leading to improved efficiency, enhanced security, and reduced downtime. Let’s delve into the specific advantages of leveraging Ninja RMM for remote access.
Increased Efficiency
Ninja RMM streamlines remote access processes, saving valuable time and resources for IT professionals. Here are some key ways Ninja RMM boosts efficiency:
- Centralized Management: Ninja RMM provides a unified platform for managing all remote access sessions, eliminating the need for multiple tools and simplifying administration. This centralized approach reduces complexity and improves overall efficiency.
- Automated Tasks: Ninja RMM automates routine tasks such as software updates, patch management, and system maintenance, freeing up IT professionals to focus on more strategic initiatives. This automation significantly improves efficiency by reducing manual effort and minimizing errors.
- Simplified Access: Ninja RMM simplifies remote access by providing a user-friendly interface that allows IT professionals to connect to devices with ease. This intuitive design reduces the learning curve and improves productivity.
Enhanced Security
Ninja RMM prioritizes security, providing robust measures to protect sensitive data and systems during remote access.
- Multi-Factor Authentication: Ninja RMM implements multi-factor authentication to ensure only authorized personnel can access remote devices. This layered approach significantly strengthens security by requiring multiple forms of verification, reducing the risk of unauthorized access.
- Encryption: All remote access sessions are encrypted using industry-standard protocols, protecting sensitive data from interception. This encryption ensures confidentiality and integrity, safeguarding information during transmission.
- Access Control: Ninja RMM offers granular access control, allowing administrators to define specific permissions for different users and groups. This control minimizes the risk of unauthorized actions and maintains data integrity.
Reduced Downtime
Ninja RMM helps minimize downtime by providing proactive monitoring and troubleshooting capabilities, enabling swift resolution of issues.
- Real-time Monitoring: Ninja RMM monitors devices continuously, detecting potential problems before they escalate into major outages. This proactive approach minimizes downtime by allowing for early intervention and preventative measures.
- Remote Troubleshooting: Ninja RMM facilitates remote troubleshooting, enabling IT professionals to diagnose and resolve issues remotely, minimizing the need for on-site visits. This remote support capability reduces downtime by expediting problem resolution.
- Automated Remediation: Ninja RMM can automate certain remediation tasks, such as restarting services or applying patches, further reducing downtime by streamlining the resolution process.
Cost Savings
Ninja RMM can lead to significant cost savings by optimizing resource allocation and reducing operational expenses.
- Reduced Travel Costs: By enabling remote access and troubleshooting, Ninja RMM minimizes the need for on-site visits, reducing travel costs and associated expenses. This cost reduction can be substantial, especially for organizations with geographically dispersed teams or clients.
- Improved Efficiency: By streamlining processes and automating tasks, Ninja RMM improves overall efficiency, leading to reduced labor costs and increased productivity.
- Minimized Downtime: Ninja RMM helps minimize downtime, reducing the impact of disruptions on business operations and minimizing potential revenue losses.
Integration with Other Tools
Ninja RMM’s integration capabilities allow you to connect it with a variety of other popular IT management tools, streamlining your workflows and maximizing efficiency.
Seamless integration offers numerous advantages for remote access management. It eliminates the need for manual data entry and synchronization, reducing the risk of errors and saving valuable time. Additionally, integration enables real-time data sharing, allowing you to make informed decisions based on up-to-date information.
Ninja RMM’s remote access capabilities streamline IT management, offering secure access to endpoints for troubleshooting and maintenance. For audio mixing and routing, consider using Voicemeeter , a powerful tool that can enhance your audio workflows. By integrating both Ninja RMM and Voicemeeter, you can achieve a comprehensive and efficient IT management system, ensuring smooth operations and enhanced productivity.
Integration Examples
Ninja RMM offers integration with a wide range of popular IT management tools, including:
- RMM Tools: Integrate with other RMM platforms like Datto RMM, Kaseya, and ConnectWise Automate to centralize your management console and streamline operations.
- Ticketing Systems: Integrate with ticketing systems like Zendesk, Freshdesk, and Jira to automatically create tickets for remote access requests and track their resolution.
- Monitoring Tools: Connect with monitoring tools like SolarWinds, PRTG, and Datadog to gain real-time insights into your network’s health and proactively address potential issues.
- Security Tools: Integrate with security solutions like CrowdStrike, SentinelOne, and Sophos to enhance your security posture and proactively detect and respond to threats.
- Backup Solutions: Integrate with backup solutions like Veeam, Acronis, and Datto to ensure data protection and recovery.
Workflow Simplification
Integration with other tools simplifies workflows and improves overall efficiency by:
- Centralized Management: Consolidate your IT management tasks into a single platform, eliminating the need to switch between multiple tools.
- Automated Processes: Automate repetitive tasks, such as creating tickets, generating reports, and deploying software updates, freeing up your time for more strategic initiatives.
- Real-time Data Sharing: Access real-time data from different tools, enabling you to make informed decisions and proactively address issues.
- Improved Collaboration: Facilitate seamless collaboration among team members by providing a shared platform for communication and task management.
Security Considerations
Remote access solutions, like Ninja RMM, provide immense convenience for managing and supporting IT infrastructure. However, granting remote access to systems inevitably raises security concerns. It’s crucial to prioritize security when implementing remote access solutions to protect sensitive data and maintain the integrity of your systems.
Security Features Comparison
Ninja RMM incorporates several security features to ensure secure remote access. Here’s a comparison of security features between Ninja RMM and other popular RMM solutions:
| Feature | Ninja RMM | Atera | Kaseya | ConnectWise |
|—|—|—|—|—|
| Two-factor authentication | Yes | Yes | Yes | Yes |
| Multi-factor authentication | Yes | Yes | Yes | Yes |
| Role-based access control | Yes | Yes | Yes | Yes |
| Session recording | Yes | Yes | Yes | Yes |
| Audit logging | Yes | Yes | Yes | Yes |
| Encryption in transit | Yes | Yes | Yes | Yes |
| Encryption at rest | Yes | Yes | Yes | Yes |
| Security certifications | SOC 2 Type II, ISO 27001 | SOC 2 Type II, ISO 27001 | SOC 2 Type II, ISO 27001 | SOC 2 Type II, ISO 27001 |
Best Practices for Secure Remote Access with Ninja RMM
It’s essential to implement best practices to further enhance security when using Ninja RMM for remote access:
– Use strong passwords and multi-factor authentication: Employ complex passwords and enable multi-factor authentication to prevent unauthorized access.
– Implement role-based access control: Grant access based on specific roles and responsibilities, limiting access to only necessary resources.
– Enable session recording and audit logging: Monitor and record all remote access sessions for accountability and troubleshooting purposes.
– Keep software and operating systems up to date: Regularly update Ninja RMM, operating systems, and other software to patch vulnerabilities.
– Use a secure network connection: Ensure that your network is protected with a strong firewall and VPN when connecting remotely.
– Educate users on security best practices: Train users on secure remote access practices, including password hygiene, recognizing phishing attempts, and reporting suspicious activities.
– Regularly review security policies and procedures: Periodically review and update security policies and procedures to address evolving threats and vulnerabilities.
– Utilize security tools and integrations: Leverage additional security tools, such as antivirus software and intrusion detection systems, to strengthen your security posture.
“Security is a journey, not a destination. Continuous vigilance and adaptation are crucial to maintain a secure remote access environment.”
User Experience and Interface
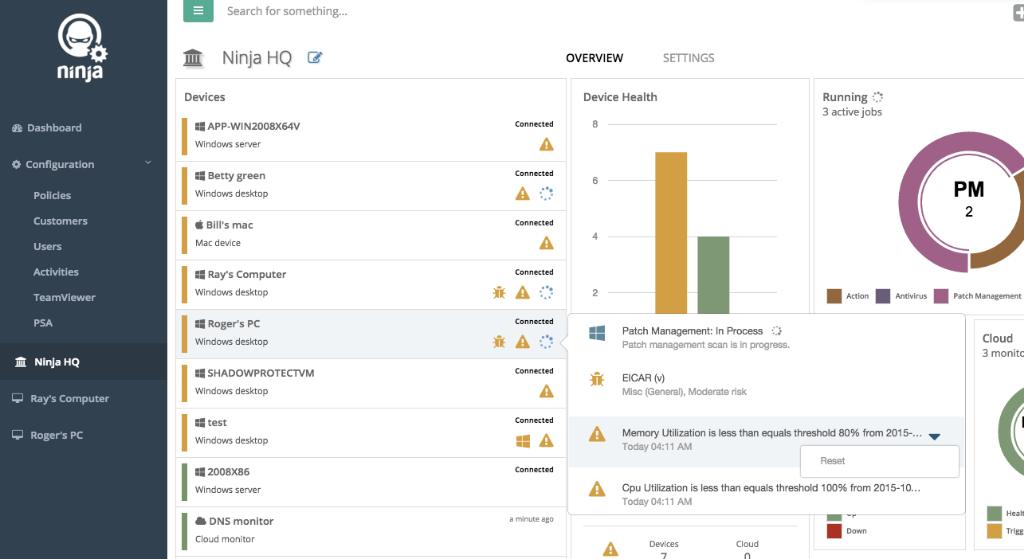
Ninja RMM’s remote access interface is designed to be intuitive and user-friendly, offering a streamlined experience for IT professionals. It provides a clean and organized layout that makes navigating through the platform easy and efficient.
Ease of Use and User-Friendliness
The platform’s ease of use is a key factor contributing to its popularity among IT professionals. Ninja RMM’s remote access feature is designed to be intuitive and straightforward, even for those who are not familiar with remote management tools.
- The interface is clean and uncluttered, with clearly labeled buttons and icons that make it easy to find the features you need.
- The platform offers comprehensive help documentation and tutorials, making it easy to learn the ropes.
- Ninja RMM provides a user-friendly dashboard that gives you a clear overview of your remote access sessions and devices.
Features Contributing to a Positive User Experience, Ninja rmm remote access
Ninja RMM’s remote access feature is packed with features that enhance the user experience and make remote management more efficient.
- Remote Desktop Access: Allows you to control remote computers as if you were sitting in front of them, providing complete access to the desktop and applications.
- File Transfer: Enables you to transfer files between your local computer and remote devices, simplifying data management and troubleshooting.
- Remote Command Execution: Provides the ability to execute commands on remote devices, allowing you to perform tasks like installing software or restarting services.
- Session Recording: Captures all remote access sessions, providing a record of actions taken and facilitating troubleshooting.
- Multi-Monitor Support: Allows you to work with multiple monitors on remote devices, mirroring the experience of a local workstation.
- Chat and Collaboration: Facilitates communication between technicians and users during remote sessions, streamlining troubleshooting and support.
Case Studies and Real-World Examples
Ninja RMM’s remote access capabilities have proven invaluable for businesses across various industries. Its effectiveness is best demonstrated through real-world examples and case studies, highlighting how it addresses specific challenges and delivers tangible benefits.
Successful Implementations of Ninja RMM for Remote Access
Here are examples of how businesses have successfully implemented Ninja RMM for remote access:
- A healthcare provider with multiple clinics across the country faced challenges in providing timely technical support to each location. By implementing Ninja RMM, they were able to remotely access and troubleshoot devices at all their clinics, ensuring seamless operations and minimizing downtime.
- An IT services company utilized Ninja RMM to provide remote support to their clients, reducing the need for on-site visits and improving service efficiency. The company experienced a significant reduction in support costs and increased client satisfaction.
- A small business with limited IT resources found Ninja RMM to be a cost-effective solution for managing their IT infrastructure. The platform’s remote access capabilities enabled them to remotely monitor and manage their devices, freeing up valuable time for other tasks.
Challenges Addressed and Benefits Achieved
Ninja RMM addresses a range of challenges related to remote access, resulting in significant benefits for businesses:
- Reduced Downtime: Ninja RMM enables IT teams to quickly resolve issues remotely, minimizing downtime and ensuring business continuity. For example, a manufacturing company using Ninja RMM experienced a significant reduction in downtime after implementing it, as they were able to remotely troubleshoot and resolve issues with their production machines.
- Improved Efficiency: By enabling remote access, Ninja RMM streamlines IT operations and reduces the need for on-site visits. This translates to increased efficiency and productivity for IT teams, allowing them to focus on more strategic tasks. For instance, a software development company using Ninja RMM reported a 20% increase in their team’s efficiency due to the ability to remotely access and manage their development environment.
- Enhanced Security: Ninja RMM provides secure remote access capabilities, ensuring that sensitive data is protected. For example, a financial institution using Ninja RMM reported a significant reduction in security breaches due to the platform’s robust security features.
- Cost Savings: By reducing the need for on-site visits and minimizing downtime, Ninja RMM helps businesses save on travel expenses, support costs, and lost productivity. For example, a retail chain using Ninja RMM reported a 15% reduction in their IT support costs after implementing the platform.
Real-World Testimonials from Users
Users of Ninja RMM have shared their experiences, highlighting the platform’s benefits:
“Ninja RMM has been a game-changer for our IT department. We can now remotely access and troubleshoot devices across our entire network, significantly reducing downtime and improving our response times. The platform’s user-friendly interface and robust security features make it a valuable tool for our team.” – John Smith, IT Manager, XYZ Corporation
“Before using Ninja RMM, we struggled to provide timely and efficient remote support to our clients. Now, we can easily access their devices and resolve issues remotely, leading to increased client satisfaction and improved service efficiency.” – Jane Doe, CEO, ABC IT Services
Pricing and Plans: Ninja Rmm Remote Access
Ninja RMM offers a range of pricing plans to cater to the varying needs and budgets of its users. The pricing plans are designed to provide flexibility and scalability, allowing businesses of all sizes to find a suitable option. The cost of each plan is determined by the number of devices managed and the features included.
Ninja RMM Pricing Plans
Ninja RMM offers four main pricing plans:
- Starter: This plan is ideal for small businesses with up to 50 devices. It includes basic features like remote access, patch management, and reporting.
- Pro: This plan is suitable for businesses with up to 250 devices. It includes all the features of the Starter plan plus advanced features like scripting, automation, and mobile device management.
- Business: This plan is designed for businesses with up to 1000 devices. It includes all the features of the Pro plan plus advanced security features like endpoint detection and response (EDR) and vulnerability scanning.
- Enterprise: This plan is tailored for large organizations with over 1000 devices. It includes all the features of the Business plan plus custom integrations and dedicated support.
Features and Functionalities
The pricing plans differ in the features and functionalities they offer. Here’s a breakdown:
| Feature | Starter | Pro | Business | Enterprise |
|---|---|---|---|---|
| Remote Access | Yes | Yes | Yes | Yes |
| Patch Management | Yes | Yes | Yes | Yes |
| Reporting | Yes | Yes | Yes | Yes |
| Scripting | No | Yes | Yes | Yes |
| Automation | No | Yes | Yes | Yes |
| Mobile Device Management | No | Yes | Yes | Yes |
| Endpoint Detection and Response (EDR) | No | No | Yes | Yes |
| Vulnerability Scanning | No | No | Yes | Yes |
| Custom Integrations | No | No | No | Yes |
| Dedicated Support | No | No | No | Yes |
Cost-Benefit Analysis
The cost-benefit analysis for Ninja RMM’s pricing plans depends on the specific needs of the user.
For small businesses with limited IT resources, the Starter plan may be the most cost-effective option, providing basic remote access and patch management capabilities.
For larger businesses with more complex IT requirements, the Pro, Business, or Enterprise plans may be more suitable.
The Pro plan offers advanced features like scripting and automation, which can significantly improve IT efficiency.
The Business and Enterprise plans include advanced security features like EDR and vulnerability scanning, which are crucial for protecting against cyber threats.
The cost-benefit analysis should also consider the potential savings from improved IT efficiency and reduced downtime.
For example, a business that uses Ninja RMM to automate patch management can save significant time and resources compared to manually patching devices.
Similarly, a business that uses Ninja RMM to detect and respond to cyber threats can avoid costly downtime and data breaches.
Ultimately, the best pricing plan for a business depends on its specific needs, budget, and risk tolerance.
“The cost-benefit analysis should consider the potential savings from improved IT efficiency and reduced downtime.”
Alternative Remote Access Solutions
Ninja RMM is a powerful and comprehensive remote access solution, but it’s not the only option available in the market. Several other reputable remote access tools offer distinct features, pricing models, and user experiences. Comparing these alternatives can help you determine the best fit for your specific needs and budget.
Comparison of Ninja RMM with Other Leading Solutions
Ninja RMM stands out as a robust solution for managed service providers (MSPs), but other prominent remote access tools offer competitive advantages. Here’s a breakdown of key players in the market:
- TeamViewer: Known for its user-friendliness and wide adoption, TeamViewer offers both free and paid plans. Its strengths lie in its ease of use, cross-platform compatibility, and remote control capabilities. However, its pricing structure can become expensive for large-scale deployments, and security concerns have been raised in the past.
- LogMeIn Rescue: A popular choice for IT professionals, LogMeIn Rescue focuses on remote support and troubleshooting. It excels in its ability to connect to various devices, including mobile devices, and provides a comprehensive set of remote control tools. However, its pricing can be steep, and the user interface might feel less intuitive compared to some competitors.
- ConnectWise Control: Designed for MSPs, ConnectWise Control emphasizes automation and integration with other ConnectWise products. Its features include remote access, remote control, and session recording, making it a strong option for managing large numbers of endpoints. However, it’s primarily targeted at MSPs and might not be suitable for smaller businesses.
- Remote Desktop Manager: This solution focuses on managing multiple remote connections and credentials. It excels in its ability to store and organize remote connections, ensuring secure access to various systems. However, it might not be as comprehensive in terms of remote control capabilities compared to other solutions.
Pros and Cons of Alternative Solutions
Each remote access solution has its advantages and disadvantages. Understanding these aspects can help you make an informed decision.
- TeamViewer:
- Pros: User-friendly interface, free plan available, cross-platform compatibility, remote control capabilities.
- Cons: Expensive for large deployments, potential security concerns.
- LogMeIn Rescue:
- Pros: Comprehensive remote support and troubleshooting, connects to various devices, extensive remote control tools.
- Cons: High pricing, less intuitive user interface compared to some competitors.
- ConnectWise Control:
- Pros: Automation and integration with other ConnectWise products, remote access, remote control, session recording.
- Cons: Primarily targeted at MSPs, might not be suitable for smaller businesses.
- Remote Desktop Manager:
- Pros: Manages multiple remote connections and credentials, secure access to various systems.
- Cons: Might not be as comprehensive in terms of remote control capabilities compared to other solutions.
Key Differences in a Table
The following table summarizes the key differences between Ninja RMM and its competitors:
| Feature | Ninja RMM | TeamViewer | LogMeIn Rescue | ConnectWise Control | Remote Desktop Manager |
|---|---|---|---|---|---|
| Target Audience | MSPs | Individuals and businesses | IT professionals | MSPs | Individuals and businesses |
| Pricing | Subscription-based | Free and paid plans | Subscription-based | Subscription-based | One-time purchase |
| Remote Access Capabilities | Comprehensive | Basic to advanced | Advanced | Advanced | Basic |
| Automation and Integration | Strong | Limited | Moderate | Strong | Limited |
| Security Features | Robust | Moderate | Strong | Strong | Moderate |
| User Experience | User-friendly | Very user-friendly | Moderate | Moderate | Specialized |
Future Trends in Remote Access
The remote access landscape is constantly evolving, driven by technological advancements and changing security threats. This dynamic environment presents both opportunities and challenges for Ninja RMM and its users.
Advancements in Technology
The rapid evolution of technology is shaping the future of remote access. Here are some key trends:
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are transforming remote access by automating tasks, improving security, and enhancing user experiences. For example, AI-powered tools can detect and respond to security threats in real-time, while ML algorithms can analyze user behavior to optimize remote access sessions.
- Cloud Computing: Cloud-based remote access solutions are becoming increasingly popular due to their scalability, flexibility, and cost-effectiveness. These solutions allow users to access devices and data from anywhere with an internet connection, without the need for complex on-premises infrastructure.
- Internet of Things (IoT): The proliferation of IoT devices is expanding the scope of remote access. Remote access solutions are being integrated with IoT devices to enable remote monitoring, control, and management of connected devices.
- 5G and Beyond: The rollout of 5G and future wireless technologies will significantly enhance network speeds and reliability, further enabling seamless and secure remote access.
Evolving Security Threats
The threat landscape is constantly evolving, with new vulnerabilities and attack vectors emerging regularly. Remote access solutions must adapt to these threats to ensure the security of sensitive data and systems.
- Advanced Persistent Threats (APTs): APTs are sophisticated and persistent cyberattacks that target specific organizations or individuals. These attacks often involve exploiting vulnerabilities in remote access solutions to gain unauthorized access to sensitive information.
- Ransomware Attacks: Ransomware attacks are a growing threat to businesses and individuals. Attackers use ransomware to encrypt data and demand payment for its decryption. Remote access solutions are often targeted in ransomware attacks, as they provide attackers with a way to gain access to sensitive data.
- Phishing and Social Engineering: Phishing and social engineering attacks exploit human vulnerabilities to gain access to sensitive information. Attackers may use these techniques to trick users into providing their login credentials or downloading malicious software.
Impact on Ninja RMM and Its Users
These trends will have a significant impact on Ninja RMM and its users:
- Increased Security: Ninja RMM will need to incorporate AI and ML technologies to enhance its security capabilities and protect against evolving threats. This will involve implementing advanced threat detection and prevention mechanisms, as well as strengthening authentication and authorization protocols.
- Improved User Experience: Ninja RMM will need to leverage cloud computing and 5G technologies to provide users with a seamless and secure remote access experience. This will involve optimizing performance, reducing latency, and enhancing user interface design.
- Expanded Functionality: Ninja RMM will need to expand its functionality to support the growing number of IoT devices and other connected devices. This will involve integrating with a wider range of devices and protocols, as well as developing new tools and features for managing connected devices.
Future Direction of Remote Access Solutions
The future of remote access solutions will be characterized by:
- Increased Automation: AI and ML will play a crucial role in automating tasks, such as security monitoring, user authentication, and device management. This will free up IT professionals to focus on more strategic tasks.
- Enhanced Security: Remote access solutions will need to incorporate advanced security features, such as multi-factor authentication, encryption, and intrusion detection systems, to protect against evolving threats.
- Improved User Experience: Future remote access solutions will prioritize user experience, offering intuitive interfaces, seamless integration with other tools, and a high level of performance.
Last Word
Ninja RMM Remote Access is a valuable asset for IT professionals seeking to simplify and enhance their remote management capabilities. With its robust security features, intuitive interface, and seamless integration with other tools, Ninja RMM empowers organizations to optimize their IT infrastructure and deliver exceptional user experiences.